This site uses cookies in accordance with our Privacy Policy.
Wordfence Research and News
Category: WordPress Security

Critical Privilege Escalation Vulnerability in Jupiter and JupiterX Premium Themes
On April 5, 2022, the Wordfence Threat Intelligence team initiated the responsible disclosure process for a set of vulnerabilities in the Jupiter and JupiterX Premium themes and the required JupiterX Core companion plugin for WordPress, which included a critical privilege escalation vulnerability that allowed any user to become an administrator.

Millions of Attacks Target Tatsu Builder Plugin
The Wordfence Threat Intelligence team has been tracking a large-scale attack against a Remote Code Execution vulnerability in Tatsu Builder, which is tracked by CVE-2021-25094 and was publicly disclosed on March 24, 2022 by an independent security researcher.
PHP Object Injection Vulnerability in Booking Calendar Plugin
On April 18, 2022, the Wordfence Threat Intelligence team initiated the responsible disclosure process for an Object Injection vulnerability in the Booking Calendar plugin for WordPress, which has over 60,000 installations.

Critical Remote Code Execution Vulnerability in Elementor
On March 29, 2022, the Wordfence Threat Intelligence team initiated the disclosure process for a critical vulnerability in the Elementor plugin that allowed any authenticated user to upload arbitrary PHP code.

Critical Authentication Bypass Vulnerability Patched in SiteGround Security Plugin
On March 10, 2022 the Wordfence Threat Intelligence team initiated the responsible disclosure process for a vulnerability we discovered in “SiteGround Security”, a WordPress plugin that is installed on over 400,000 sites.

Reflected XSS in Spam protection, AntiSpam, FireWall by CleanTalk
Update – after this article was published, Denis Shagimuratov of CleanTalk reached out to us on Twitter.

Increase In Malware Sightings on GoDaddy Managed Hosting
Today, March 15, 2022, The Wordfence Incident Response team alerted our Threat Intelligence team to an increase in infected websites hosted on GoDaddy’s Managed WordPress service, which includes MediaTemple, tsoHost, 123Reg, Domain Factory, Heart Internet, and Host Europe Managed WordPress sites.

WordPress 5.9.2 Security Update Fixes XSS and Prototype Pollution Vulnerabilities
Last night, just after 6pm Pacific time, on Thursday March 10, 2022, the WordPress core team released WordPress version 5.9.2, which contains security patches for a high-severity vulnerability as well as two medium-severity issues.
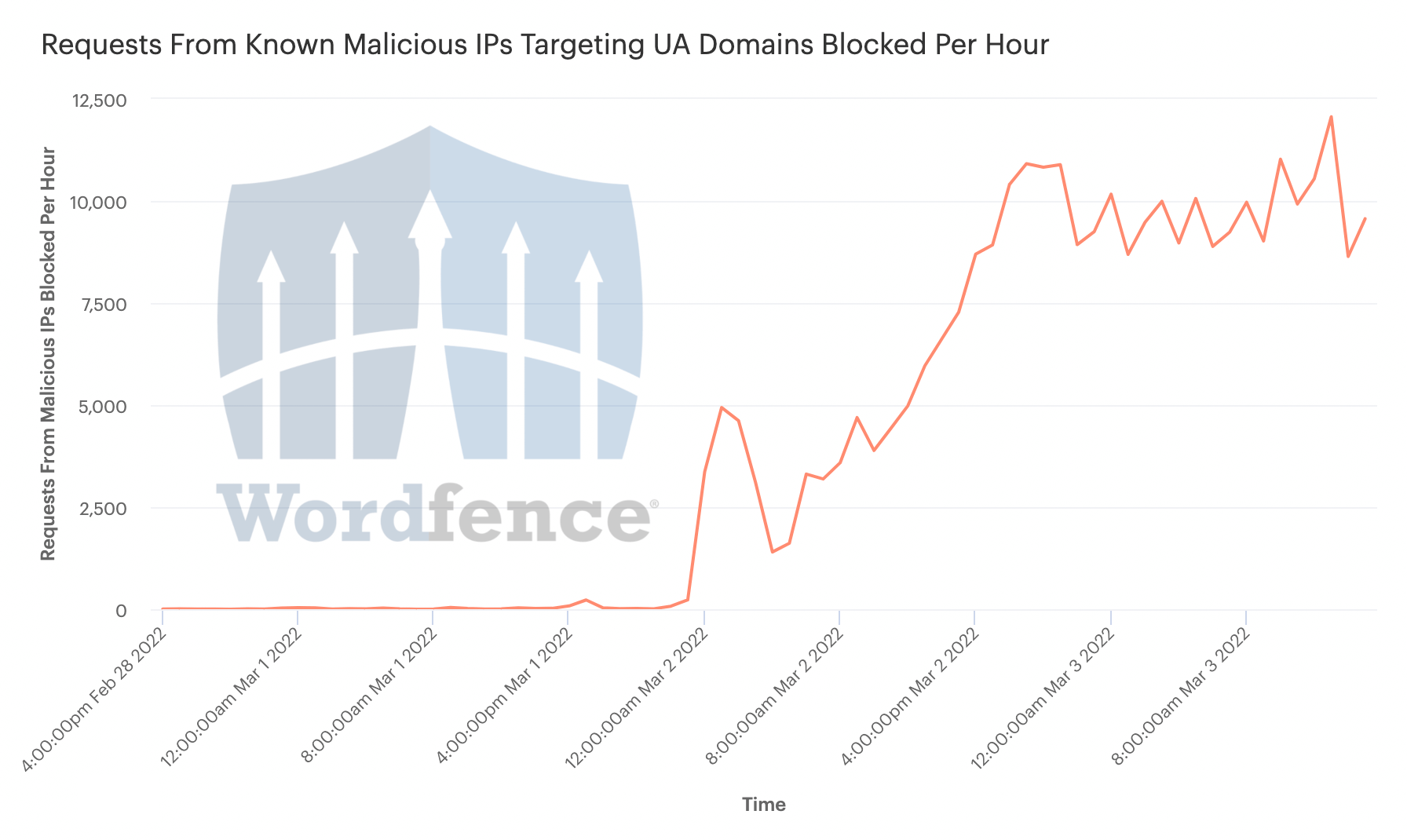
We’re Now Blocking 10,000 Requests Per Hour in Ukraine From Known Malicious IPs
48 hours ago we deployed our commercial real-time threat intelligence automatically, and for free, to all Ukrainian websites with the .UA top-level domain.

Ukraine Universities Hacked As Russian Invasion Started
Note: This article has been updated to reflect that the hosting provider “Njalla”, which routed the malicious traffic involved in this attack, is based in Sweden, not in Finland, although IP geolocation data indicates that the specific server that the traffic transited may be based in Finland.
