This site uses cookies in accordance with our Privacy Policy.
Wordfence Research and News
Category: Wordfence

Details of an Additional File Deletion Vulnerability – Patched in WordPress 4.9.7
Today WordPress released version 4.9.7, a security release which addresses two separate arbitrary file deletion vulnerabilities requiring Author privileges.

Optimizing Wordfence Security Settings: Brute Force Protection
As a part of the Wordfence Client Partner initiative, we’ve recently had some in depth conversations with organizations using Wordfence at scale.
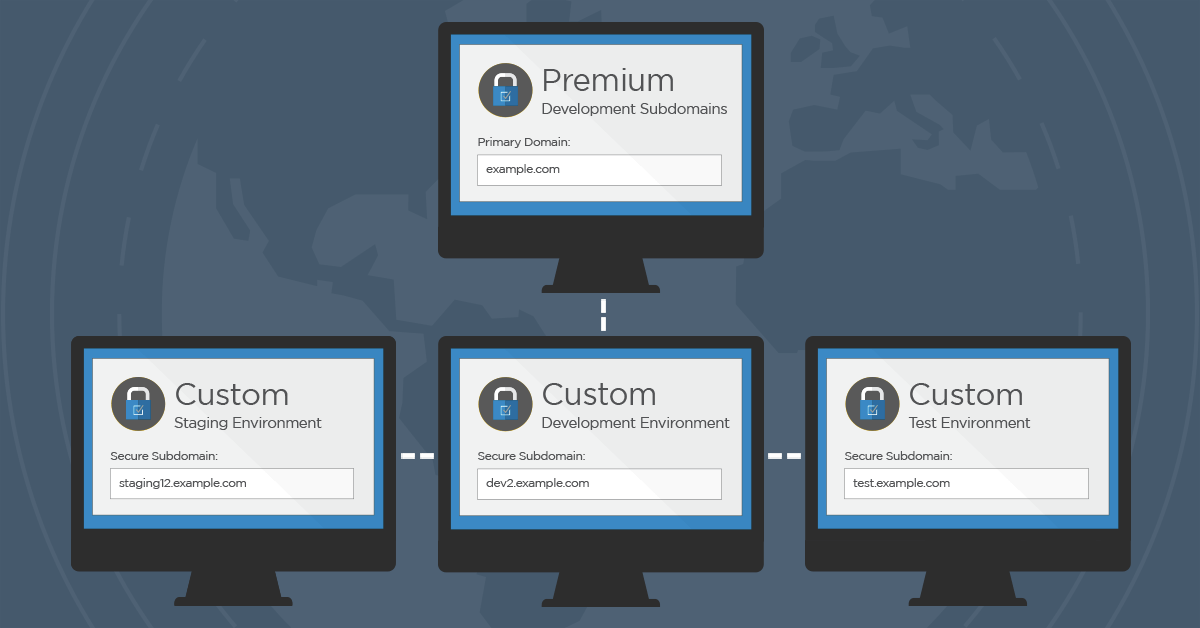
New Feature: Custom Premium Development Subdomains
Two weeks ago we announced the release of a new Wordfence feature that automatically allows Wordfence Premium customers to use their premium license key to secure a specific list of staging, development or test subdomains.
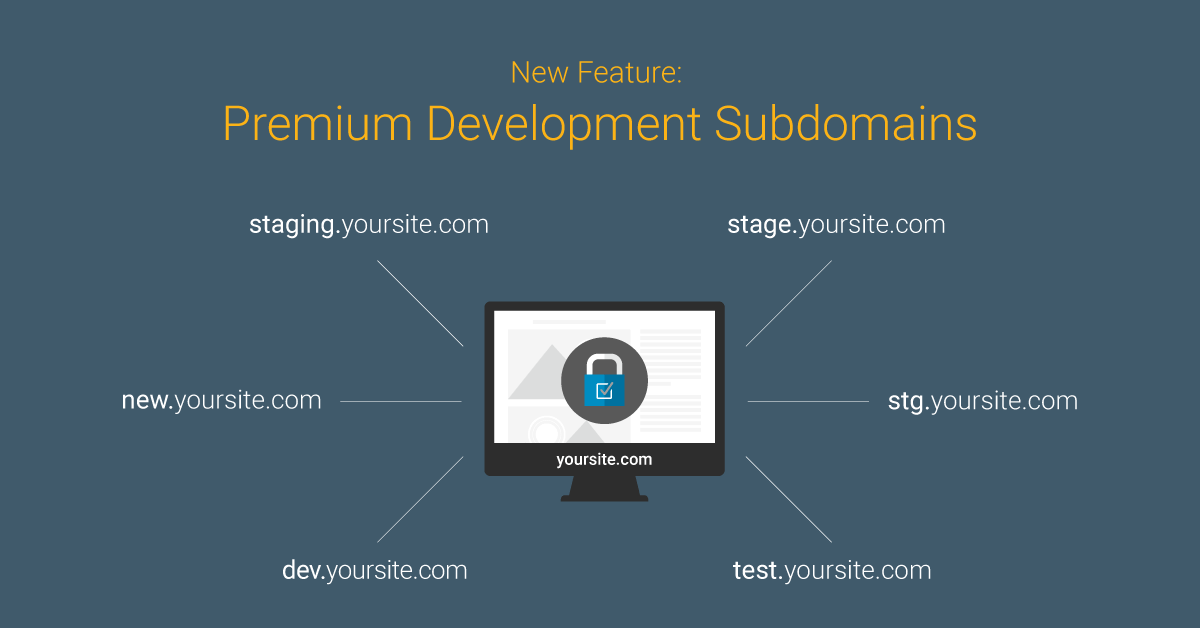
New Feature: Premium Development Subdomains
For our premium customers using staging, development, or test subdomains for managing their site’s updates and development, we are happy to announce the ability to utilize premium licenses across subdomains for a premium installation of Wordfence.

Wordfence Is GDPR Compliant
Last Updated December 1, 2021 As of September 27, 2021, the revised EU Standard Contractual Clauses issued by the EU Commission on June 4, 2021 (in effect as of June 27, 2021) apply to all Defiant, Inc.
How the Wordfence Scanner Protects Your Site
When we think about Wordfence and how it improves your WordPress security posture, there are two core features we tend to focus on: the firewall, and the security scanner.

Wordfence GDPR Update 2: On Target For May 25th
Update: Wordfence is now GDPR compliant. Click here to learn more.

Introducing Discounted Hacked Site Cleanings
Last month we introduced ‘high demand’ pricing for our site cleaning service.
Wordfence and GDPR: How The Defiant Team Are Preparing For GDPR
Update: Wordfence is now GDPR compliant. Click here to learn more.
WordPress: Tracking Emerging Cryptomining Threats
This is a post written by James Yokobosky who works on the Defiant Threat Intelligence team.
