Dissecting a Clever Malware Sample for Optimized Detection and Protection
As part of our product lineup, we offer security monitoring and malware removal services to our Wordfence Care and Response customers. In case of a security incident, our incident response team will investigate the root cause, find and remove malware from your site, and help with other complications that may arise as a result of an infection. During the cleanup, malware samples are added to our Threat Intelligence database, which contains over 3.5 million malicious samples. In some good news, we find that the vast majority of cleans are conducted for new clients who sign up for Care or Response after realizing their site has been compromised.
Additionally, we accept malware sample submissions at samples@wordfence.com and have numerous other sources for obtaining new malware samples. If you ever come across a piece of malware that is undetected by Wordfence, please send it in to us so that we can write a signature for it.
In more good news, Wordfence already detects most new and existing malware with our current signature set. However, sometimes new malware cleverly attempts to evade the Wordfence scanner, and our team combats this by writing new detection signatures that are released to Premium, Care, and Response customers in real-time, and released to customers still using the free version of Wordfence after a 30 day delay.
Today, we would like to showcase one sample of malware from our Threat Intelligence Database, which was first added in July 2021 as part of a malicious zip file containing web shells.
Analyzing the Sample
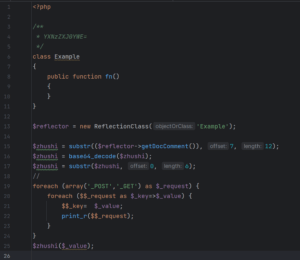
At the start of the file, this malware sample declares an Example class, which is preceded by a rather odd-looking comment. After the class declaration, there is the instantiation of a new ReflectionClass, which can be used to gather information about another class. More specifically, the $reflector variable can be used to obtain information about the Example class.
The variable $zhushi is declared on line 15. Its content is set to the string YXNzZXJ0YWE= which is obtained from the comment of the Example class. It is then base64_decoded, resulting in the string assertaa before being truncated to store the string assert in the variable $zhushi.
On line 19 the script loops through all $_POST and $_GET parameters and outputs them to the screen. After completion of the loop, the variable $_value contains a string that is under the attacker’s control.
On line 25 the script makes use of a PHP feature called a variable function. If a variable is succeeded by a parenthesis, PHP will attempt to execute a function with the same name as the string contained in the variable itself. In this case, the function call will be assert($_value); where $_value can be anything the attacker would like it to be and is set in one of the $_GET or $_POST parameters previously mentioned. Prior to PHP 8, an assert statement would simply be evaluated using the eval() function which results in remote code execution.
There are many use cases for this type of malware. An attacker could spread an infection by using this script to replicate itself on the infected site, making successful removal more difficult. It could be used to infect other files, upload new malware, send spam when it is invoked, or launch login attempts to other web sites in the hopes of spreading malware beyond the infected website’s server.
Sometimes malware samples are part of a bigger picture, but in this case we are dealing with a simple web shell. Obfuscation is usually added to malware in order to evade detection.
How We Detect It
One common pitfall when using signature-based detection for malicious code is to write signatures that are too specific in an attempt to avoid false positives. One such attempt might be to look for the variable name $zhushi and immediately flag the sample as malicious. Evading detection would be as simple as changing the variable name.
Our team of malware signature authors remains aware of this pitfall so instead, we focus on the discussed features and behavior of malware, like this piece of malware, in order to improve our detection capabilities.
This particular sample as well as a few other of its variants are covered by our production signature set as a custom signature was released back in 2021. However, as a reminder, new malware signatures are made available to Premium, Care, and Response users in real time. Customers still using the free version of Wordfence receive access to our malware signatures with a 30 day delay.
Conclusion
In today’s post we discussed the inner workings of a web shell and showed how it uses several obfuscation techniques to try and disguise its real purpose and evade detection. That wasn’t enough to stop our team from being able to write detection for this piece of malware. Our Premium, Care, and Response users as well as those who are still using the free version of Wordfence are protected by our malware scanner during file uploads against the upload of this sample as well as some of its variants. This means that Wordfence will block any attempts by attackers that try to upload this file to a compromised WordPress site. Properly configured scans running on those sites will also detect this sample in the unlikely event it is uploaded to a site during an infection.
It is important to remember that detection of a compromise is just as important to security as ensuring your site remains protected. By using the Wordfence plugin, ensuring it has been optimally configured and by following security best practices, you are ensuring your site remains as protected as possible. Nothing can ever be 100% secure, and risk can never fully be mitigated, so it is important to have monitoring on your site in the event it is compromised despite following all best practices. The Wordfence scanner will alert you to any infections so you can initiate an incident response, and also block malicious malware uploads in the event an attacker gets past a site’s first line of defense.
If you believe that your site might be infected, you can enlist the help of our Incident Response team by purchasing our Care or Response offering, or follow this guide to remove the infection yourself.
If you have a malware sample that was missed during a Wordfence scan, please let us know by sending the sample to us at samples@wordfence.com.


Comments