Not Just for the Government: Using the NIST Framework to Secure WordPress
When setting up a WordPress website, it is easy to focus on the look and feel of the website, while overlooking the important aspect of security. This makes sense, because the security of a website is largely invisible until something goes wrong. Installing a cybersecurity plugin like Wordfence significantly reduces the chances of a successful attack on a WordPress site. What no software can fully protect is the human element. This is where cybersecurity models and frameworks come in. We discussed one cybersecurity model, the CIA Triad, a few months ago. There are other models and frameworks that each have their own strengths and weaknesses, depending on how they are implemented.
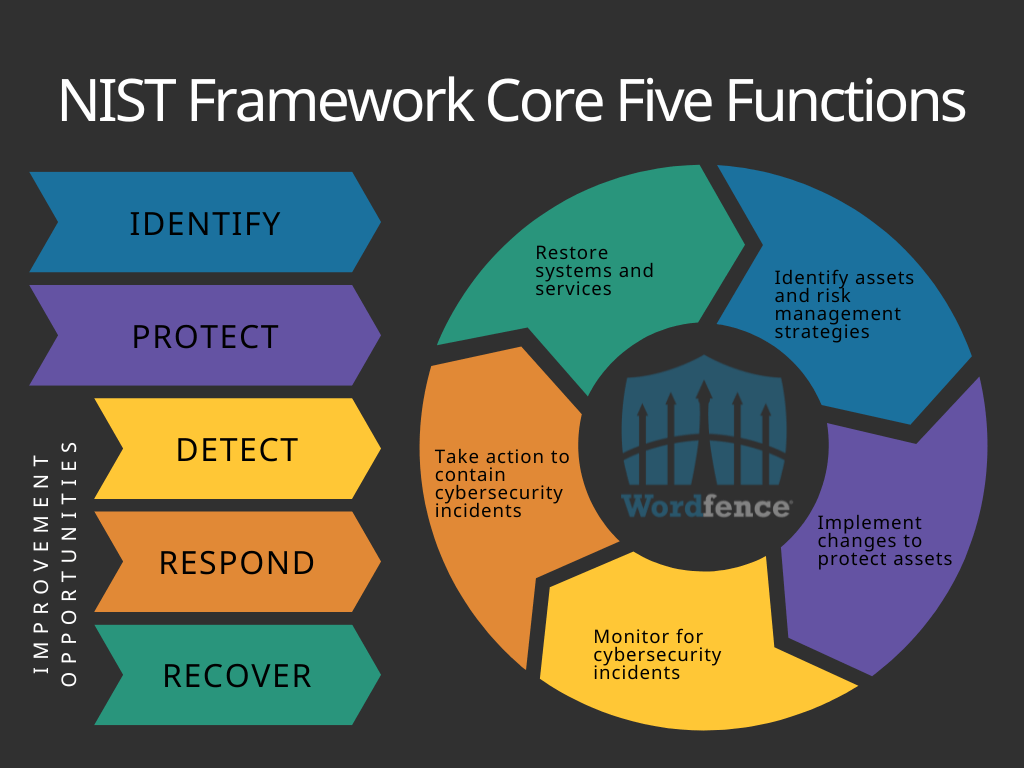
Cybersecurity frameworks are a common tool used by organizations to protect their networks, systems, and digital assets. One well-known framework is the National Institute of Standards and Technology (NIST) Framework Core, which consists of Five Functions. While the NIST Framework Core is often associated with securing government networks, the same principles apply to WordPress websites as well.
The Five Functions in the NIST Cybersecurity Framework Core are identified as the Identify, Protect, Detect, Respond, and Recover phases. Each phase describes an important aspect of securing an organization’s physical and digital assets. Rather than a list of dos and don’ts, these were written to be guidelines that help in making decisions that affect organization’s risk management. The best way to view this is as a cycle that is repeated whenever there is a cybersecurity incident or change to the protected assets.
Identify
The Identify function helps to identify any assets that need some form of cybersecurity protection. This includes physical assets like servers, digital assets like software, and even people. In this phase, it is important to make a list of all assets and the maintenance or security that they require. Any time there is a cybersecurity incident, or a change to the physical or digital systems in place, this phase should be revisited to ensure that changes are accounted for. New cybersecurity measures are considered in this phase, taking into account both individual systems, and how those systems interact with each other.
WordPress websites have many parts, both physical and digital. Even if a site is not hosted on a server that is physically controlled by the site owner, the server itself must still be a consideration of the site owner. Choosing a host that is trusted and has a record of using proven cybersecurity practices helps to ensure that the chances of a compromise of the server itself is minimized. If a malicious actor is able to access a compromised server, they may be able to make changes that can lead to modification of website files and databases, as well as locking the site owner or administrator out of their hosting environment control panel. One method of maliciously controlling accounts through a compromised host was discussed in our breakdown of the Anonymous Fox F-Automatical script, where part of the script could be used by threat actors to change passwords on compromised WHM or cPanel accounts which can help a threat actor to maintain persistence.
In addition to physical assets, all software used needs to be accounted for as well. On a WordPress site, this means WordPress core, themes, and plugins. Any underlying technologies may also need to be cataloged. If not managed by the host, then the site owner will also need to ensure that appropriate updates processes and cybersecurity considerations are taken into account for the web server software (Apache, Nginx, etc.), the PHP version, and any other software the site relies on for proper operation. Once all physical and digital assets have been cataloged, appropriate cybersecurity measures will need to be determined.
Protect
The Protect function guides the implementation of resources that will reduce the impact of a cybersecurity incident and prevent it from spreading. It is one thing to catalog your assets and determine appropriate cybersecurity measures, but those measures also must be implemented in order to be effective. Physical security will be implemented in this phase as possible, and any site administrator will be implementing digital security security solutions, such as Wordfence Premium, to protect against existing and new threats to the website. With these measures in place, threat actors can be stopped before their attacks have a chance at success, and malware can be quickly removed from an infected website.
Based on the most recent 12 months of data, the Wordfence firewall detects and blocks an average of 4,603,076,842 attack attempts across 4 million protected websites every month. In the year of data reported here, the Wordfence firewall blocked 30,488,640,718 attack attempts based on identified malicious activities, and 24,748,281,391 attempted password attacks. This means that on average more than 1,100 attack attempts are thwarted against each website every month, without any negative impact to the website. If websites with vulnerabilities or administrator accounts with weak or leaked passwords were left unprotected, they could be used in data theft schemes, as a platform to disseminate malware, or for a number of other malicious purposes.
Regular maintenance is a large part of the Protect phase as well. One of the best ways to keep WordPress websites secure is to keep WordPress, themes, and plugins updated with the latest security updates. Additionally, the software behind the website, like Apache and PHP, will need to be maintained as well. Whenever possible, best practice may be to enable automatic updates. If automatic updates are not possible, it is important to regularly check for available updates and manually update as soon as possible after a new version with security fixes is released.
Along with any physical and digital security measures, it is also important to keep in mind the people behind the website. Anyone who assists in managing the website will need to be considered an asset, and a potential cybersecurity risk. This means implementing access controls like user roles and two-factor authentication (2FA), utilizing the principle of least privilege by limiting access to roles, and training anyone who helps in the management of the website on cybersecurity best practices.
Detect
The Detect function outlines and implements methods, systems, and software that help to identify a cybersecurity incident rather than allowing it to continue unseen. Detection is one of the most important steps in keeping a website safe, as the unseen cannot be stopped. Regular scanning of files is critical, as is monitoring of website traffic. If malicious behaviors are detected prior to a malicious payload being delivered, then an attack can be rendered ineffective before it can truly begin.
It is important to run regular scans for malware on your website. Wordfence includes one of the industry’s largest WordPress-specific malware databases to scan websites and alert administrators of any malware found in their website files. The Wordfence Scanner detects malware from an average of 173,449,409 files each month. Armed with the scan results, administrators may be able to identify infected core, plugin, or theme files that need to be reinstalled.
Monitoring website traffic can also help to detect threats. Wordfence Live Traffic monitors and tracks all activity on the website, logging the IP address, location, time, browser, and page being visited by any human or bot accessing the website. After reviewing traffic, the administrator has the option to dive deeper into the details of a specific visitor or even block the IP to prevent its access in the future.
Respond
When a cybersecurity incident has been detected, the Respond function supports organizations in determining the appropriate actions needed to contain the incident. It is not enough to simply detect an incident, plans and measures need to be in place to contain an incident before it becomes an even bigger issue. If a threat actor can be stopped in the process of inserting a malicious admin user, then they won’t have the access to complete further attacks such as collecting website subscriber data or other sensitive information.
Responding to an incident may be something that can be handled by the website administrator, or they may need help from a team of cybersecurity experts. For more complex infections, or if the administrator is not familiar with how to respond to a malware threat, our team of analysts can use the scan data as a starting point to investigate and respond to malware that has been found on websites protected by Wordfence Care or Wordfence Response.
Recover
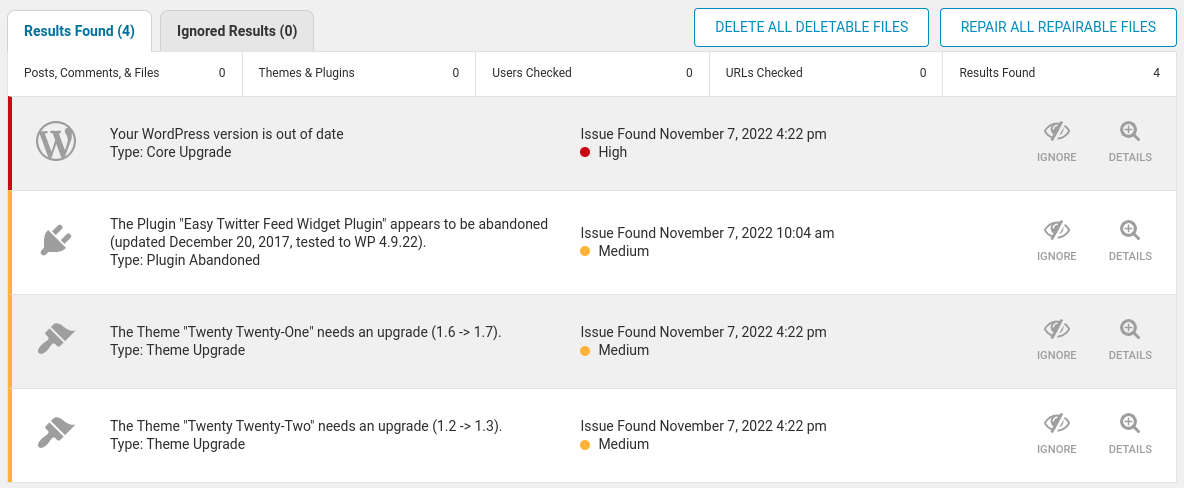
The final phase is the Recover function, which guides the recovery process after a cybersecurity incident, reducing the time required to return to normal operations. Cybersecurity incidents can modify the content or functionality of a website, requiring content to be restored from backup, themes or plugins to be reinstalled, or even running updates or installing new software to protect against the vulnerability that was exploited. Maintaining an awareness of available updates helps to ensure vulnerabilities are patched as quickly as possible, which is why Wordfence lists any available updates right on the Wordfence Scan Results page. Updating after an incident can prevent a recurring incident by applying any available security patches, but regularly updating software can prevent successful exploits of vulnerabilities before there can be a first incident.
NIST Cybersecurity Framework Core Implementation Tips
Implementing a cybersecurity framework might feel like a daunting task, however it is often easier than it might initially seem. We have some suggestions that can help with implementing the NIST Cybersecurity Framework Core on WordPress websites.
Start with the highest priority
When cataloging systems and software, keep in mind that not all assets are of equal priority for a cybersecurity solution. If the website exists on a shared or managed server solution, the host will often have cybersecurity measures in place to protect the physical systems and even some of the base software. This allows site owners to focus on the software they are installing, which means that WordPress specific cybersecurity solutions will be the first priority for many WordPress website administrators.
Be flexible
When writing policies and procedures, it is not always possible to account for every scenario that may be encountered. When a situation arises that does not fit into existing policies and procedures, the situation needs to be reviewed and existing policies and procedures will be updated to account for the new situation.
Ensure policies and processes are clearly defined
Policies and processes are an important part of any holistic cybersecurity solution. It is important to make sure that these are clearly defined, with as much detail as possible to avoid confusion if an incident occurs. Clearly defined policies and processes can also help prevent human error that could lead to a cybersecurity incident.
Follow up on policies
Effective policies are not “set it and forget it” solutions. It is important to regularly review policies, as well as regularly discuss them with any individuals who have a hand in managing the website or other systems. This helps to keep policies fresh in people’s minds, which increases the chances of policies being followed and cyber incidents being avoided.
Communicate
This tip cannot be stressed enough. Communication is the backbone of any good cybersecurity plan. Employees or anyone else who has a hand in developing and managing the website needs regular and clear communication about cybersecurity expectations and procedures. When an incident occurs, communication must be accurate and concise, and should include any stakeholder including customers and website visitors. Clear and honest communication can help to work through an incident faster, as well as build trust in how the situation is being handled.
Review and learn
Any time there is a cybersecurity incident, all five phases of the NIST Cybersecurity Framework Core need to be revisited, with policies, procedures, and solutions being reviewed for possible improvements. Any identified improvements need to be implemented as quickly as is safely possible. This is not the time for snap decisions, but taking several months to discuss options is also not going to be effective. After every incident or change, review what happened and how it happened, and learn from what went well and what could have been improved.
Use tools
Installing a cybersecurity solution like Wordfence to protect WordPress websites helps to stop incidents before they start, and recover quickly from incidents that have already occurred. Wordfence, including Wordfence Free, provides a number of tools to help you implement the NIST Cybersecurity Framework Core, including two-factor authentication (2FA) to help secure user accounts and alerts for suspicious activity and outdated components. The Wordfence firewall detects and blocks malicious activities, while Wordfence Scan detects malware and other indicators that website data may have been compromised.
Wordfence Premium includes the most up-to-date firewall rules and malware signatures, as well as our Real-Time IP Blocklist to block malicious actors based on IP addresses known to be performing malicious activities. Wordfence Care and Wordfence Response include a security audit to help identify opportunities to improve website security, and suggest best practices alongside incident response in the event a site has a security incident.
Conclusion
In this post we discussed how to apply the NIST Cybersecurity Framework Core to the protection of WordPress websites. Implementing the use of the NIST Cybersecurity Framework Core will help any website administrator to ensure that their website is secure, and that policies and procedures are in place to keep the website secure as software changes or vulnerabilities are discovered. When a cybersecurity incident occurs, they will be able to use the framework to help recover from the incident as quickly as possible to minimize the impact of the incident.
This article was written by Topher Tebow, a former Wordfence Threat Researcher.





Comments
9:27 pm
Great article. Based on this I am building a spreadsheet so that when my customer asks again about a cyber security report, I can have something ready more in line with NIST requirements.
One thing I think you missed out is the server data and dependencies. A great place to find those is in the Wordfence diagnostics tab. Having an easy to find list of php, mySQL versions etc is great. You even have OpenSSL versions in there which is very useful at the moment!
11:58 am
Thank you, Simon. The Wordfence diagnostics tab is definitely a great suggestion for creating an inventory of your server technologies and dependencies, as well as monitoring the versions for available updates.