Optimizing Wordfence Security Settings: Brute Force Protection
As a part of the Wordfence Client Partner initiative, we’ve recently had some in depth conversations with organizations using Wordfence at scale. These conversations have been enlightening, and we wanted to share some of the stories we’ve heard about how different organizations use Wordfence.
Wordfence is the most robust security solution available for WordPress site owners, and the number of security features available is unparalleled. This ensures that Wordfence can be customized to be an optimal security solution for your specific environment and security needs.

Getting Started with Wordfence
When you install Wordfence for the first time, the plugin defaults to recommended settings that are a perfect starting place for customization. You won’t need to do much else. However, Wordfence is highly configurable, allowing you to tailor how it works to meet your needs.
How our Customers Use Brute Force Protection:
Wordfence includes a number of powerful brute force protection features that can be used to prevent malicious bots from gaining access to your site, including the integration with Troy Hunt’s version 2 of the Pwned Passwords API that prevents access using passwords previously seen in a breach. In this post we will focus on Brute Force Protection and how our customers can customize this feature, based on their security needs.
Factors to consider when modifying your site’s Brute Force Protection settings include:
- How adept are your users? Do you have users that forget their passwords often? Are they logging in sporadically and have a high probability of losing their passwords? You’ll want to take them into consideration and allow room for user error.
- Is this a high traffic, high profile site that often experiences hacking attempts?
- Is your site under repeated attack from brute force attempts?
The following customer scenarios serve as great real-world examples of how Wordfence can be customized to meet specific needs.
Kyle’s Agency Customer Site
One of our agency partners, Kyle, manages a number of WordPress installations for his customers. His customers rarely perform any administrative tasks, but they have editor access in order to add and modify new content. The agency has administrator access, and they have set up Wordfence Premium to protect the site. In addition to the premium features of country blocking and two-factor authentication for administrators only, he has tightened Brute Force Protection. Some of his customers often forget their passwords, and he wants to ensure they can still access the site to post content without causing too much administrative work for his team.
Kyle sets up his sites so that failed logins lockout after 5 attempts, forgot password attempts are set to 10 and a user is locked out for 24 hours. He does not set the site to immediately lock out invalid usernames, but he immediately blocks anyone who uses ‘admin’, ‘administrator’, or any other failed logins he sees. He routinely audits his site’s failed logins and adjusts this setting accordingly.
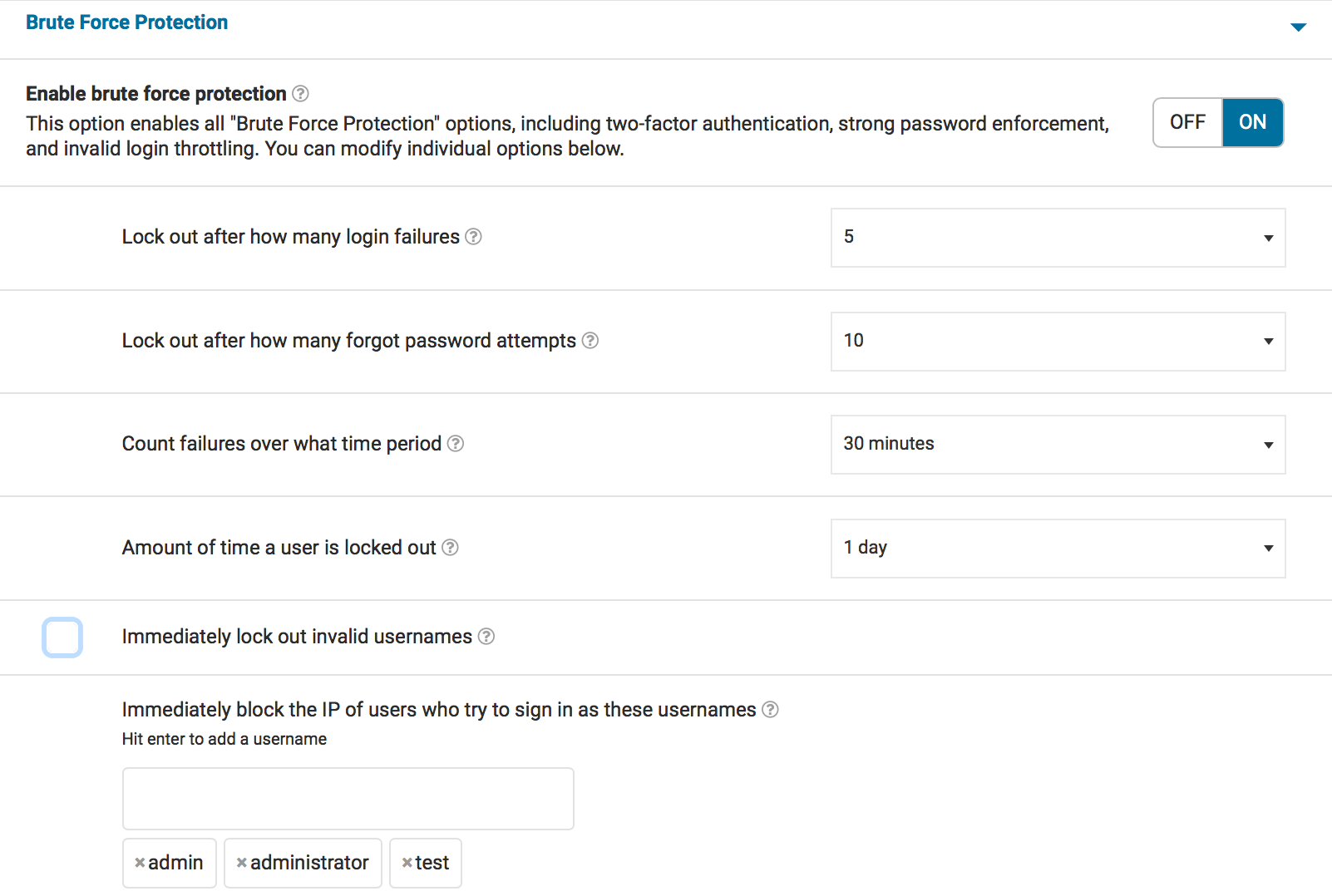
Maria’s Membership Site
Maria uses Wordfence on a WordPress membership site. She has a team of publishers and administrators and a large number of members who need to login in order to access content. Some of them use good password hygiene, but others do not. Maria’s site is also protected by Wordfence Premium, and she has made some adjustments to her brute force protection settings.
Maria has set her failed logins lockout to 5 attempts, forgot password attempts are set to 10, and a user is locked out for 24 hours. She does not set the site to immediately lock out invalid usernames because she has a large user base. She immediately blocks anyone who uses ‘admin’ or ‘administrator’, but does not go further than that. She uses Wordfence Premium’s two-factor authentication and some minor country blocking to augment her site’s security.
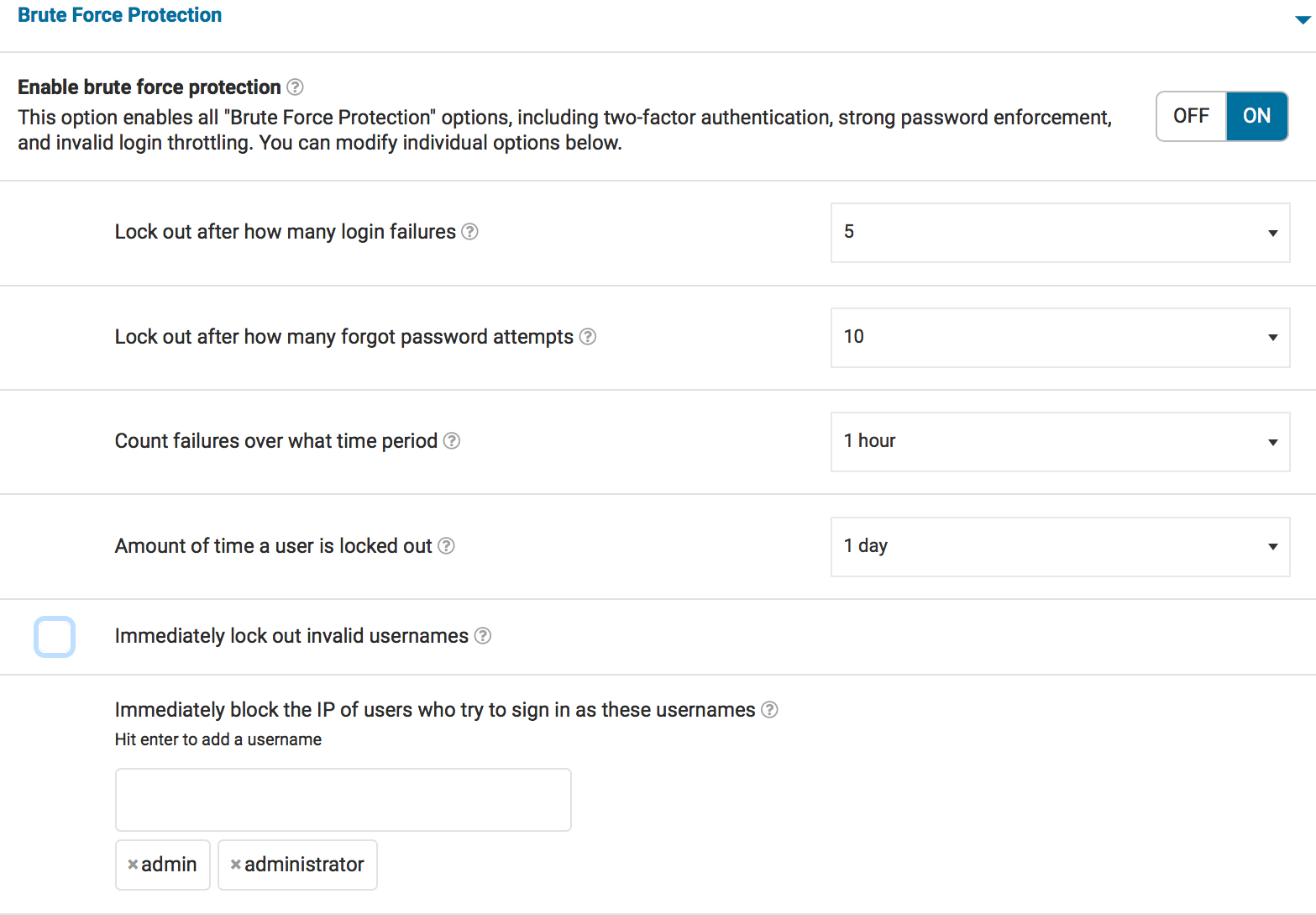
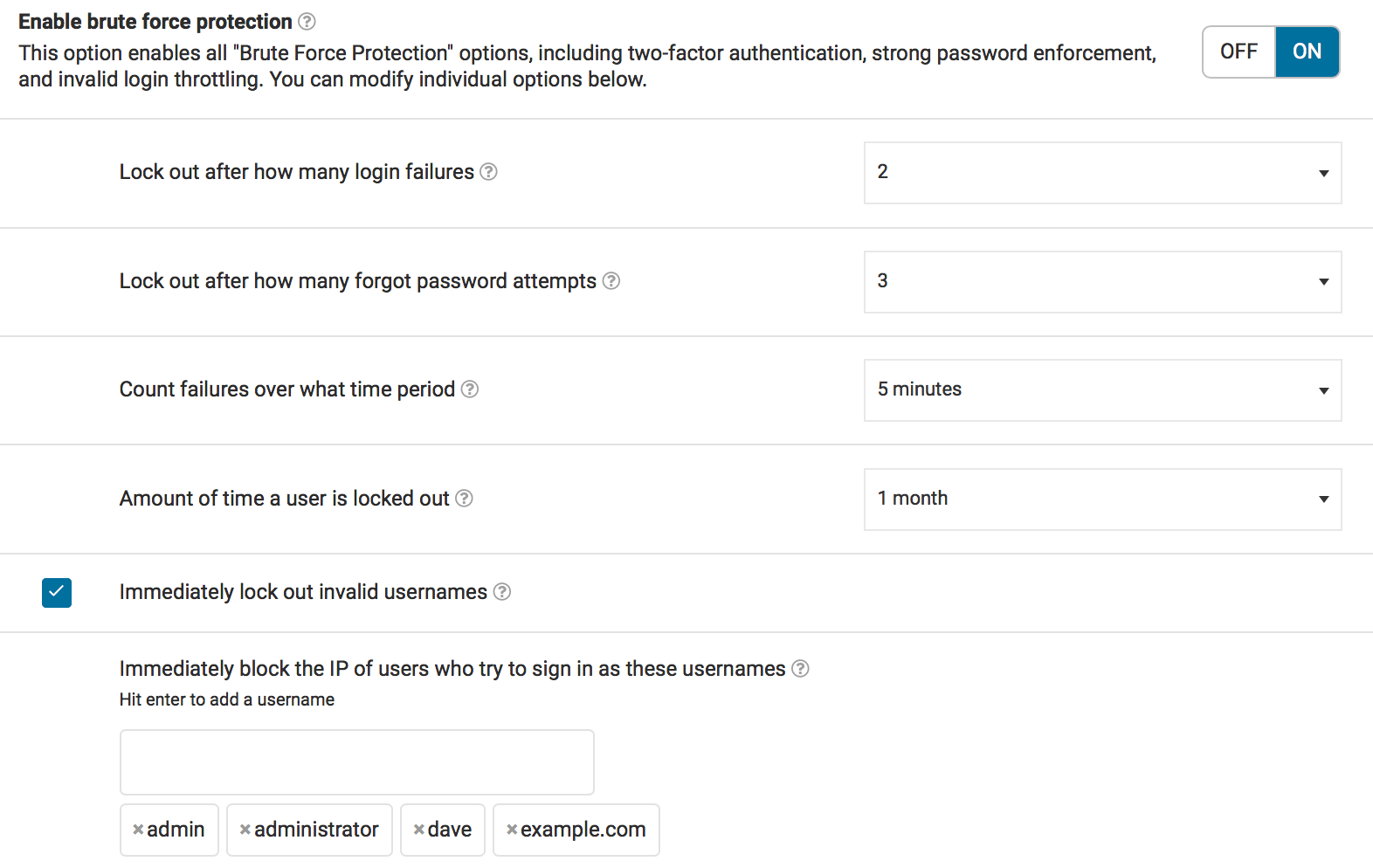
Dave’s Personal Site
Dave has a personal blog. He has one login for himself and no other users. He knows his password, and also has access to FTP in order to easily deactivate Wordfence if he ever locks himself out. He has tightened his Brute Force Protection settings because he’s quite confident in his ability to store his password safely.
Dave sets up his sites so that failed logins lockout after 2 attempts, forgot password attempts are set to 3, and IP addresses that reach these limits are locked out for one month. He immediately locks out any invalid users and also immediately blocks anyone who uses ‘admin’, ‘administrator’, or any other failed logins he sees.
He also uses two-factor authentication to ensure that logging in is difficult for anyone other than himself should his credentials ever be discovered.
Sam’s Small e-commerce Site
Sam has a small e-commerce site that is growing rapidly. He has a number of contractors on the site updating product information. He has users that need to login for various business functions and needs to ensure that everyone can log in, but doesn’t want to risk his site’s security given how sensitive e-commerce data is. He’s invested in Wordfence Premium and requires his administrators to use two-factor authentication for logging in.
Sam sets up his sites so that failed logins lockout after 5 attempts, forgotten password attempts are set to 5, and a user is locked out for 4 hours. He does not set the site to immediately lock out invalid usernames. He has set his Wordfence installation to block any passwords from data breaches to anyone who can publish as well as administrators because of the turnover in the contractors he is using to update product information.

How are you using Brute Force Protection?
We hope this deeper look at our Brute Force Protection settings has been helpful. If you’ve been using Wordfence for a while, how are you using Brute Force Protection? Are there rules you’ve set that work well for your unique site requirements?
Are you seeing any new brute force attack patterns that concern you? Let us know in the comments.
We’ll be covering more ways that our customers use Wordfence in upcoming posts.

Comments
11:03 am
I don't know where this magic number of 3 attempts comes from. It is way too tight. All of us occasionally have a fleeting mental block or really can't remember, what was the password for this site? 7-9 attempts is much more reasonable. Any serious hacker trying break in is not going to stop at 3 attempts. I then block any true hacker for 24 hours. I also ban or blacklist admin or administrator.
To be honest I use all in one WP security in addition. It gives me double protection.
No doubt WordFence is a truly great vital plugin
3:20 pm
Thanks for sharing your settings, Philip! Each site is so different, which is why Wordfence gives you the power to set things up however you wish. Wordfence really does provide all you need in order to secure your site. With the benefit of Wordfence Premium and the real-time blacklist, the protection you receive for your WordPress site is unparalleled.
11:17 am
We (the agency) are the only people accessing the site, so we lock out pretty everything immediately for 5 days should anything be wrong.
We also monitor the failed attempts and add recurring usernames from there to the immediate block list.
We also receive email alerts when logins fail - this is good practice, but causes a lot of emails being received...
One thing - we run a standard list of usernames that people try (admin, administrator, Admin, Administrator, test, Test, a, A, b, B, and so on). In the old version of Wordfence, we could copy that list and paste it into each new install for immediate blocking. Now, we have to add them one by one - so we don't do it. Can we have the old "one per line" input back so we can paste 50 or 60 usernames at once? Thanks!
Great job in general by the way! Wordfence is great.
David
12:46 pm
Hi David, thanks for the feedback! Yes, if you're able to tighten who is accessing the site and are sure of their technical capabilities, tightening brute force protection makes perfect sense. I've passed on your request; we've also got some new features coming soon that will help managing your large install base much easier. Stay tuned! And thanks for the feedback about Wordfence. We're always looking to improve your experience and help you keep your clients' sites safe.
12:48 pm
David, one other note: You can copy and paste a comma-separated list into the field and the Wordfence plugin will detect this and split the usernames up. It's not as easy to copy the list from one site to another, but if you've got the list in a text file, you can definitely still input the list of usernames to block.
11:23 am
I generally have a set of default blocks for for every site which covers the most commonly used/attempted login accounts, then add any others after that which get regular hits.
The most common of those include :
admin
administrator
root
user
qwerty
test
test1234
domain.tld
domain
domainadmin
admindomain
testing1234
testing
Obviously replacing the word "domain" with the equivalent for the site. Other than that I used very similar to the above with 2 / 3 lock outs in relation.
12:42 pm
Thanks for sharing your technique, Adam! We love hearing about how our agency partners are using Wordfence. That is a great collection of logins to block.
2:02 pm
There's one thing that I haven't really found an explanation for when it comes to blocking login attempts. I don't quite understand the need for blocking specific usernames that are invalid from the outset.
If you allow someone to keep trying say 'admin', will that not just keep them trying that username in a futile way, rather than encourage them to try a different username?
What is the actual benefit?
3:16 pm
As well as securing the administrative portion of WordPress, blocking brute force attack also protects site availability. Every login request requires a database connection and query to validate the request. As these attacks are usually automated, a brute force attack can overwhelm server resources with repeated requests. Site owners often use Wordfence to block the most common usernames to discourage brute force attacks from affecting their site's availability for valid visitors. Thanks for asking, Ray!
3:35 pm
And using your hint in reply to David, here's the comma-separated list for anyone that wants to use it:
admin,administrator,root,user,qwerty,test,test1234,domain.tld,domain,domainadmin,admindomain,testing1234,testing
9:01 pm
Thanks Kathy
I didn't think of that aspect and it makes total sense.
3:39 am
I just noticed under General Wordfence Options: Disable Code Execution for Uploads directory. I turned it on. Is there any reason not to turn it on?
I am using Wordfence with Multisite and I am the only one who has access other than a programmer. Between LastPass and Chrome remembering my passwords, I never have a problem accessing the site. I can also easily disabled Wordfence by FTP if I need to.
I use the following settings:
Lock out after how many login failures: 2
Lock out after how many forgot password attempts: 2
Count failures over what time period: 30
Amount of time a user is locked out: 2 months
8:58 am
Hi Philip! That would be dependent upon your particular installation. Review your plugins and ensure they're not using that directory for functionality. If not, you should be safe to disable code execution.
3:41 am
I also block all countries other than the US, since I am only interested in traffic from the US. My programmer is in India, so I unblocked India when he is doing work.
11:35 am
Thanks for your useful post. It really helps me out to set my custom setting on my personal website. I am using Wordfence free version and still enjoy it a lot.