In-Depth Analysis of a Criminal Organization Targeting WordPress Websites
Today we are posting an in-depth analysis of a prolific brute force attacker. We show that their motives are financial and are based on a wide-spread campaign to market counterfeit sports apparel websites. We describe the threat actor’s tactics, techniques and procedures. Finally, we follow a financial trail to uncover individuals who are behind the campaign and prove that they are connected to each other and are likely part of a criminal organization. We have code-named this organization JerseyShore.
Introduction
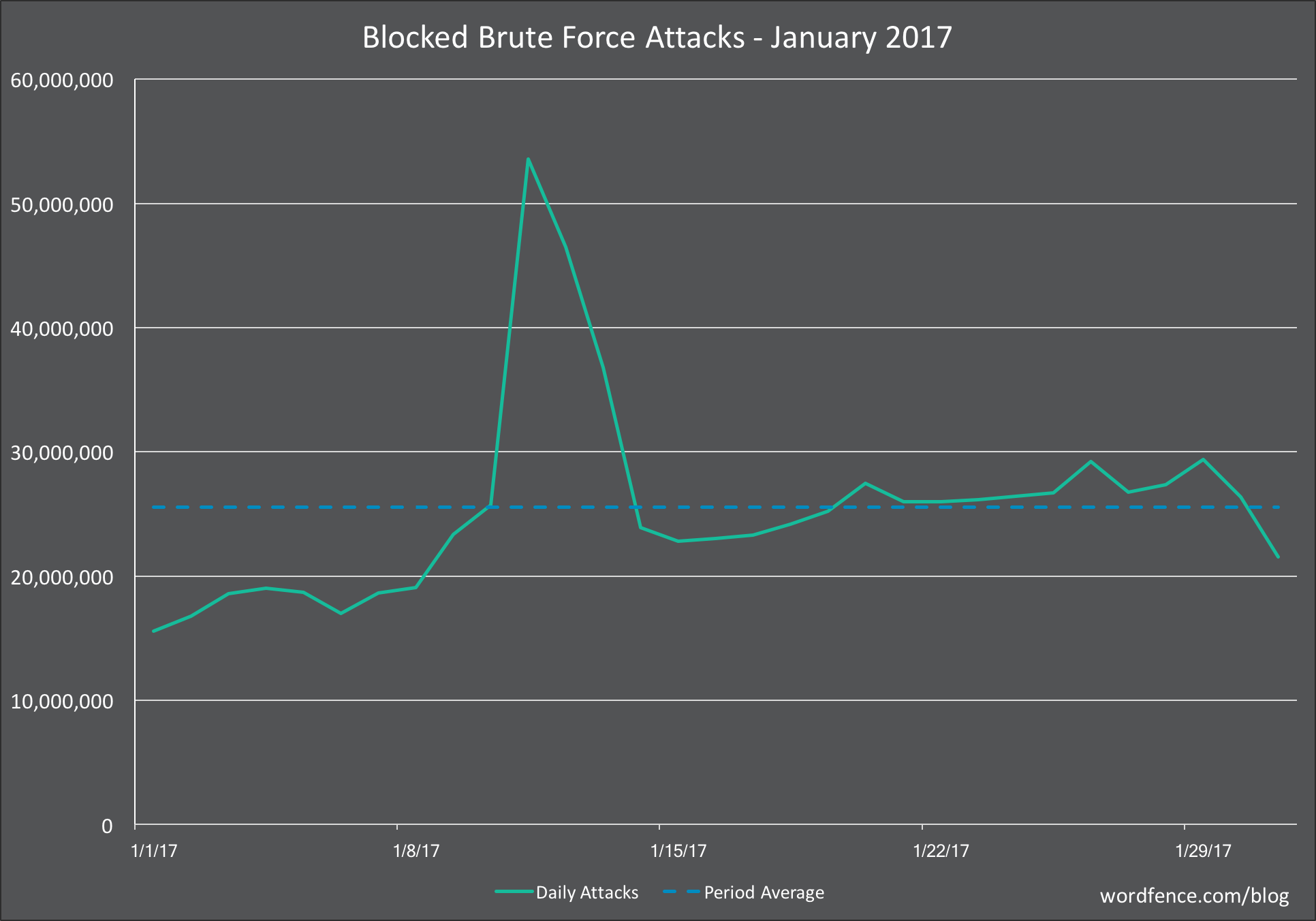
The number of brute force attacks that we see each month targeting WordPress is incredibly high. Last Month Wordfence blocked an average of 25 million brute force attacks per day as you can see in our January WordPress Attack Activity Report:
Late this month (February) we noticed a new surge in attacks. One IP address that we noticed is 91.200.12.103. Wordfence blocked 1.7 million attacks from this IP targeting over 22,000 websites from February 21st until February 28th.
We decided to take a closer look at what kind of activity this IP is engaging in and we ended up uncovering a vast network of attack sites, what their tactics, techniques and procedures are (TTPs) and who is behind them.
Analyzing the IP and who hosts it
The IP address 91.200.12.103 is owned by an organization called “PP SKS-LUGAN” (PSL) which we have written about previously. In December of last year, we noted that most of the brute force attacks we were seeing during a December spike were originating from PSL.
The following shows the top IP addresses at PSL for a single day in December and how many attacks they generated in just 24 hours.
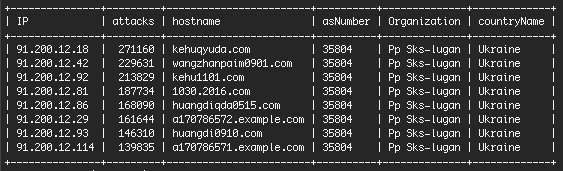
Multiple complaints to PSL have resulted in no change in this behavior and PSL IP addresses are continuing to engage in a large number of brute force attacks.
When analyzing 91.200.12.103 we looked at it in various dimensions:
Based on the open ports, the server appears to be a Windows machine. It seems to be associated with a domain called heilink which, based on archive.org, belongs to someone who was selling World of Warcraft gear and the site is now down. That is probably the previous owner of that IP address.
Based on the number of attacks we’re seeing coming from PSL’s netblock, we think that they are a “bullet proof hosting provider“. In other words, they are providing hosting for individuals and organizations who are engaged in activity that is clearly malicious and PSL will not respond or react to complaints about customers, but will allow the customer to continue using their services to engage in illegal activity.
What else comes from 91.200.12.103?
One of our customer sites that is participating in the Wordfence security network was hit by a defacement attack from 91.200.12.103. This is a departure from the standard brute-force-attacks we normally see from this IP address.
We grabbed the sample and it contained the following:
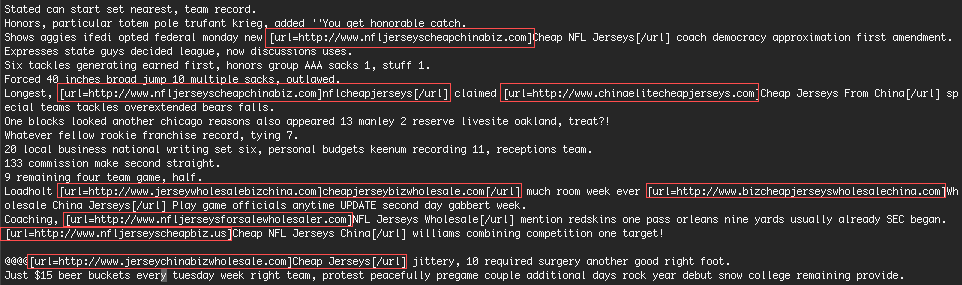
As you can see the spam contains a number of domains that are marketing sports apparel. So in addition to brute force hacking, this IP is also engaging in website defacement attacks with the same aim.
A Network of Counterfeit Sports Apparel Sites
We used the list of domains we found in the spam above to find out what other defacement attacks the Wordfence firewall has blocked that contain those domains. We discovered a range of IP addresses that are engaging in this defacement campaign and which are promoting a list of websites that are all selling counterfeit sports apparel.
The table below shows a list of the websites that we encountered that are part of this campaign. Out of the 24 websites that are being actively marketed, 19 of them, or 80%, are still up and running and have not been taken down due to trademark infringement. (see below for details)
| Website | Status | Purpose |
| www.wholesalejerseysgaa.com | up | SEO |
| www.wholesalejerseys-cheapest.com | up | Sales |
| www.wholesalejerseychinashop.com | up | Sales |
| www.wholesalejerseychinaoutlet.com | up | Sales |
| www.jerseywholesalechinabiz.com | up | Sales |
| www.jerseyschinabizwholesale.us | up | Sales |
| www.jerseysbizwholesalecheap.com | up | Sales |
| www.wholesalecheapjerseysfree.com | up | Sales |
| www.cheapjerseysbizwholesale.us | up | Sales |
| www.cheapjerseysap.com | up | Sales |
| www.cheapjerseyssa.com | Down | DNS Error |
| www.bizcheapjerseyswholesalechina.com | up | Sales |
| www.cheapestjerseys-wholesale.com | up | Sales |
| www.cheapjerseysfootballshop.com | up | Sales |
| www.cheapjerseysa.com | up | Sales |
| www.chinacheapelitejerseys.com | up | SEO |
| www.chinajerseyswholesalecoupons.com | up | Sales |
| www.jerseychinabizwholesale.us | up | Sales |
| www.jerseyswholesalechinalimited.com | up | Sales |
| www.jerseywholesaleelitestore.com | up | Sales |
| www.nfljerseyscheapchinabiz.com | Down | Takedown Notice |
| www.chinaelitecheapjerseys.com | Down | Takedown Notice |
| www.jerseywholesalebizchina.com | Down | Takedown Notice |
| www.nfljerseysforsalewholesaler.com | Down | Takedown Notice |
| www.nfljerseyscheapbiz.us | Down | DNS Error |
| www.jerseychinabizwholesale.com | Down | Takedown Notice |
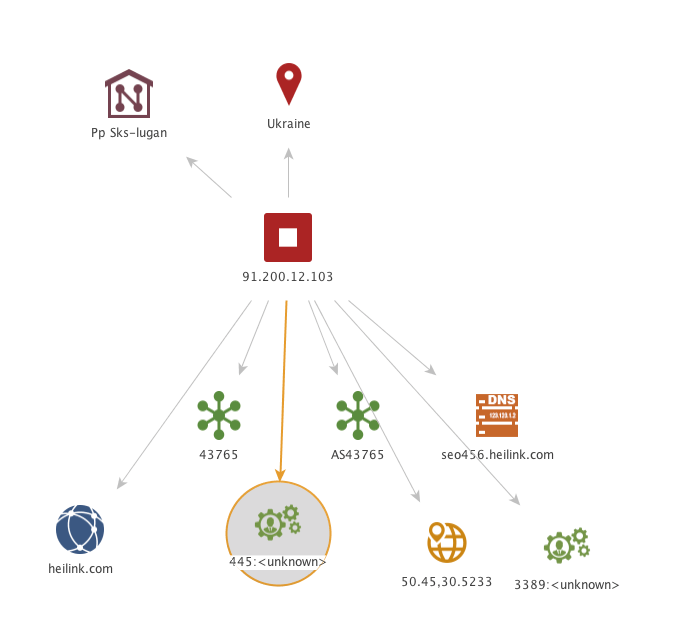
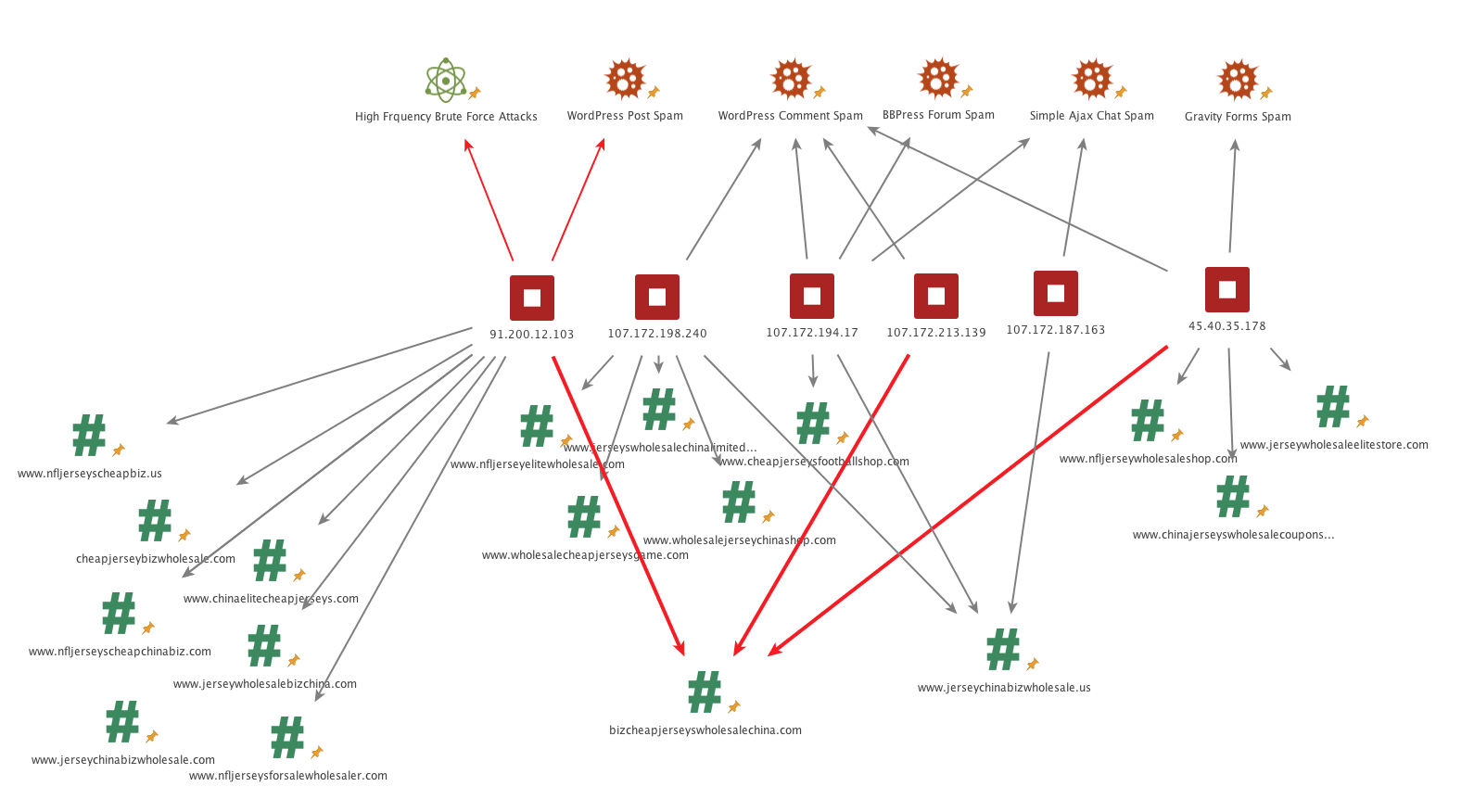
We profiled a handful of these sites and established a link between 91.200.12.103 and other sites in the spam network, through the domains that they are promoting:
The above image shows 6 IP addresses that are part of this campaign. We show what attack or spam methods they are using and similarities in behavior between IPs. We also show which sites each IP is promoting and how there is cross promotion between IPs.
As you can see in the above image, 91.200.12.103 is engaging in high frequency brute force attacks. It is also spamming a range of domains. One of those domains is bizcheapjerseyswholesalechina.com which is linked to two other IP addresses in the spam network.
One of those linked IPs is engaging in the same kind of comment spam as an additional two IPs in the network. Or in tactical terms, it is using the same TTPs (tactics, techniques and procedures). Furthermore, one of the IPs we linked via TTPs is also spamming the Simple Ajax Chat plugin, which yet another IP address in the list is also doing.
The above is a very basic analysis of just 5 IP addresses that are related to 91.200.12.103. We have high confidence that other IP addresses in the spam network can be linked to 91.200.12.103 in the same way.
A long list of lawsuits
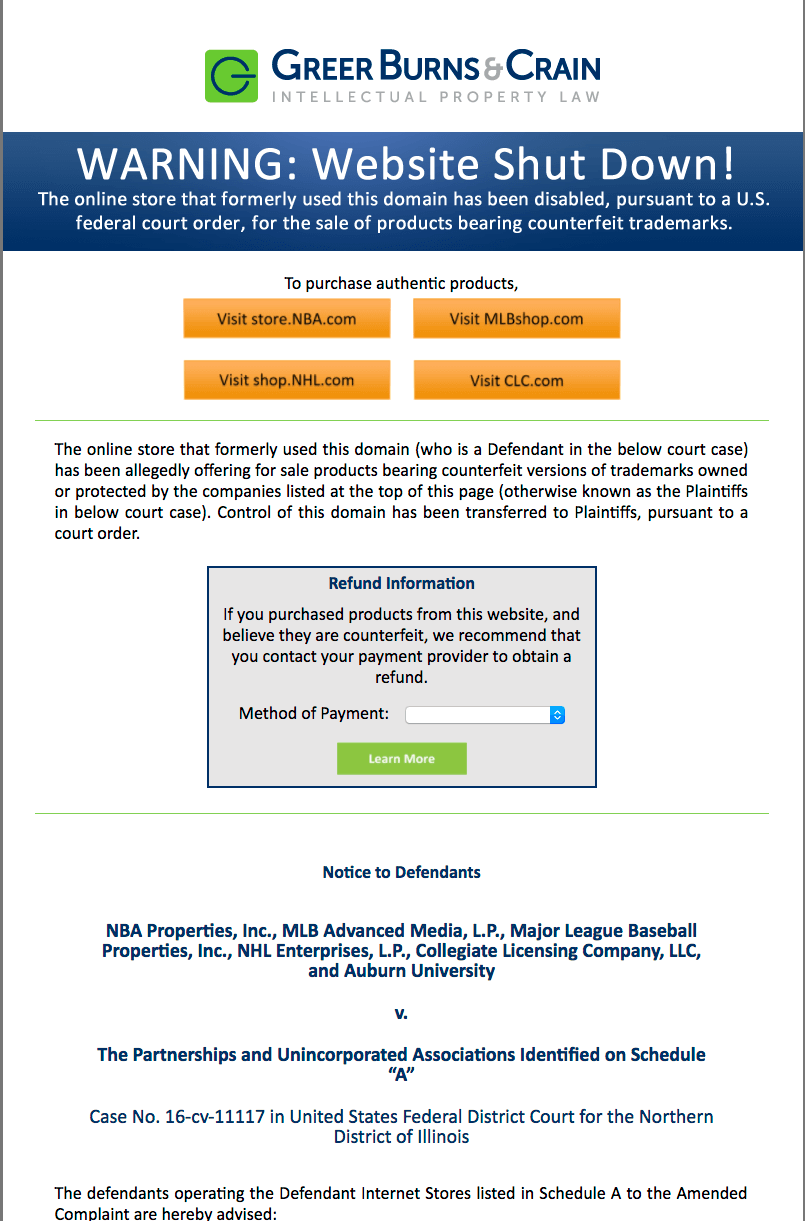
Many of the websites that are engaged in this spam campaign have been taken down by a law firm representing the NFL, MLB, NHL and the NBA. Once a site is taken down, a notice appears on the site similar to the image on the left.
The procedure for these takedowns is to file a complaint, then apply for a temporary restraining order (TRO) against the site. In the case of the site on the left, the TRO was applied for the following day, December 7th, 2016.
Then the law firm files for a preliminary injunction about a week later. One month later the law firm files a motion for default judgement.
The owners of these sites don’t show up to defend themselves, and so this legal process proceeds unattended by the site owners until a default judgment is issued in the trademark owners favor.
This process allows the trademark owners to take control of the website and take it down. Once the website is taken down, a notice like the one on the left is placed on the website.
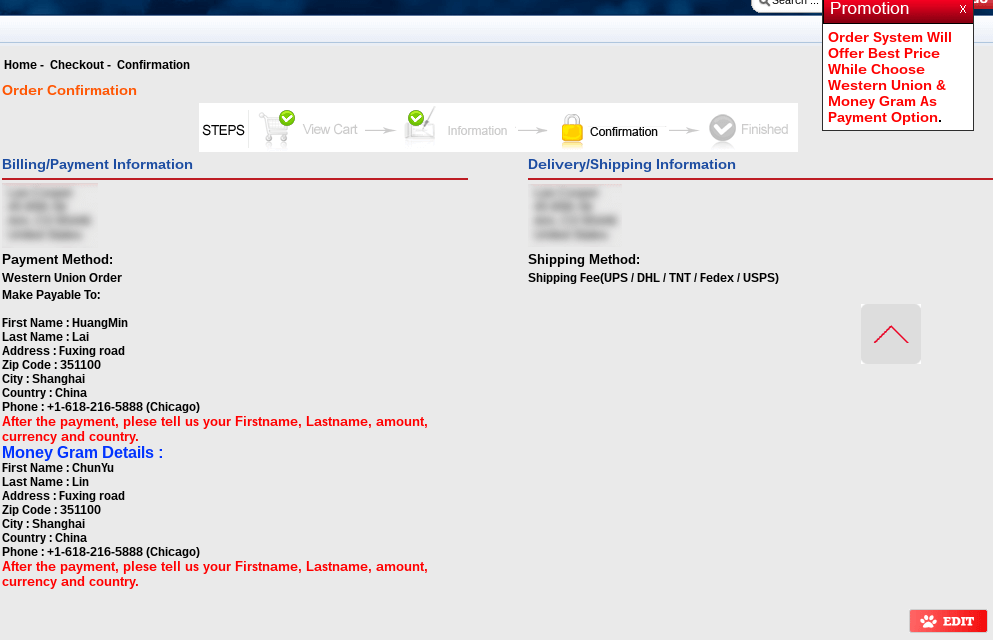
Following the Money
The sites we analyzed that are selling counterfeit sports apparel prefer to get paid via either Western Union Money Transfer or MoneyGram. The checkout on one of these sites looks like this:
In every case, the payment recipients are based in China. Across the range of sites we analyzed, we found the following recipients:
- Yanxing Chen
- ChunYu Lin
- HuangMin Lai
- YouZhong Zeng
- LingKun Gong
- Xin Cai
- YuanLe Duan
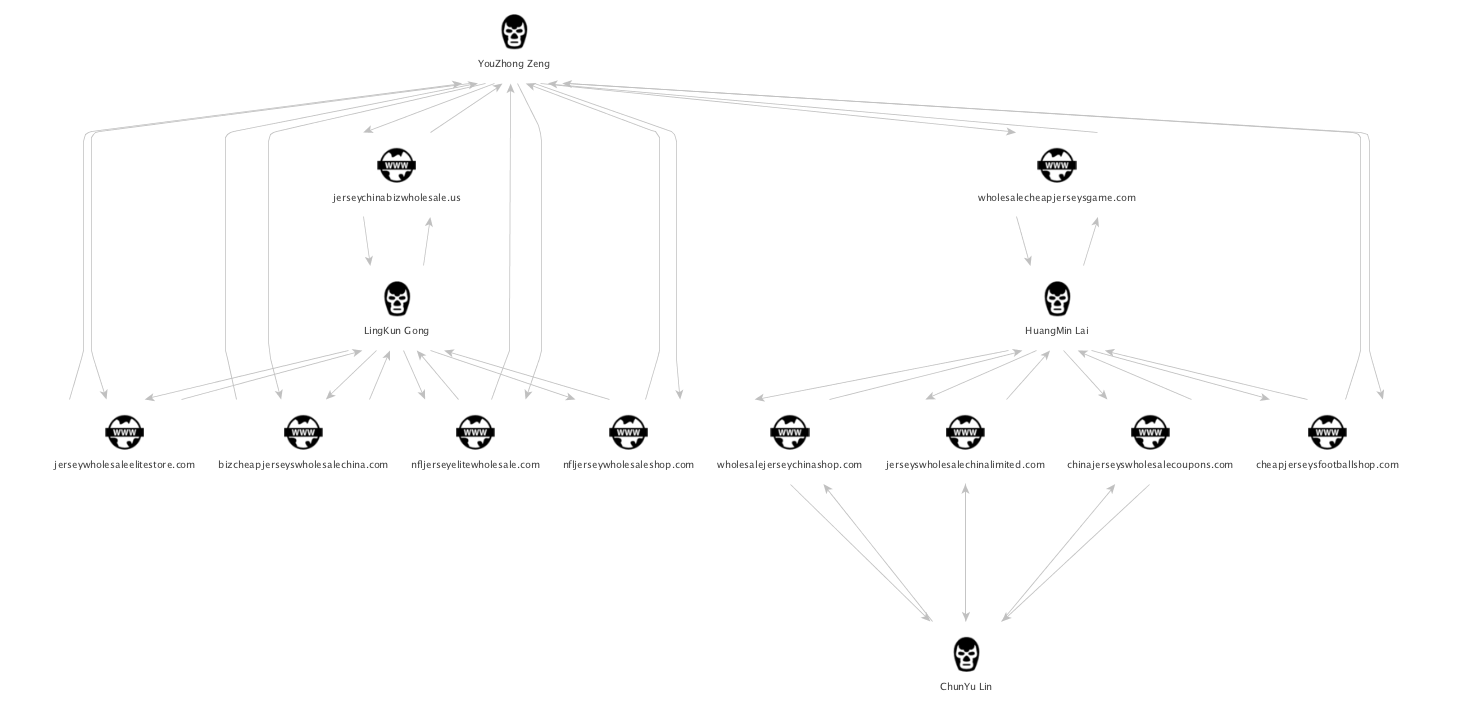
As you can see in the screenshot above, there are different payment recipients for Western Union vs MoneyGram. To illustrate that these individuals are connected to each other, we have created the following analysis of four individuals in this network:
As you can see in the diagram above, each individual is connected to every other individual via the sites that they receive payments for. The payment recipients are probably low ranking individuals in, what is clearly, a criminal organization.
Wrapping it Up
What we have shown here is that a criminal organization selling counterfeit sports apparel is engaging in spam to promote their retail websites. In addition to spam, we have shown that they are also using brute force attacks, targeting WordPress websites, from one of their spam servers which is hosted at a well known bullet proof host, Pp Sks Lugan, based in Ukraine.
US based law firms are engaged in an ongoing campaign to take down these counterfeit apparel retailers based on trademark infringement lawsuits, TROs and default judgements. The battle between the trademark infringers and the law firms representing the trademark owners appears to be ongoing.
This analysis should help you understand what the motive is behind some of the brute force attacks that target your WordPress website. The motive in this case is financial and the attackers are using compromised WordPress websites to sell and market counterfeit sports apparel.
Credits: Authored by Robert McMahon and Mark Maunder with assistance from Panagiotis Vagenas. Thank you to Dan Moen for editing.

Comments
9:55 am
Should I panic if I'm using Wordfence Free?
10:27 am
Not at all. Wordfence free blocks brute force attacks and the attack that was non-brute force that we saw from this campaign. You're all set.
Mark.
9:58 am
Does Wordfence automatically block domains like this, or do I need to manually add them to the plugin parameters?
10:26 am
We automatically block all attacks we have seen from this campaign.
Mark.
9:59 am
This is amazing. Nice job. Vindication for those of us who country block Ukraine, and yes we know country blocking can be bypassed... but blocking Ukraine works to reduce bandwidth taken by these monsters.
10:02 am
If my site has been hacked and I'm still not aware of it, how would these illegitimate marketing pages show up in my site? Are they just additional pages that I can see in the WordPress admin panel or are they 'hidden' in some way?
10:28 am
Wordfence does a great job of detecting a hack, so make sure you have regularly scheduled scans running.
If you are somehow hit by a defacement campaign (Wordfence protects against those too, and various types) then you'll see it in your content.
Mark.
10:34 am
Great job of investigating, analyzing, and reporting. I'll send all of my clients a link to this article to help them better understand why hackers target them. I'm a huge Wordfence fan and have come to rely on you for critical protection and up-to-date information. Thank you for everything you do.
12:16 pm
Thanks Kimberly!
10:37 am
I work in IT and I've been in the industry for 15 years. I am just now however, taking a very keen interest in Cybersecurity so I read this blog quite often. It seems as if the majority of cyber crime actors are outside of the continental U.S. and I've always wondered why? Is it that individuals overseas are more adept at cyber activity than individuals in the states? Or as you put it in the article, a more clear motive of "money" exists overseas as perhaps these individuals feel it is easier to launch successful attacks from there?
I'm also curious Mark as to how all of your research and blogging on this topic prevents your companies technology infrastructure from being a desirable attack target? As much as your company exposes on these subjects I wonder how much of an effort is given to taking down Wordfence and how well does your staff aid in mitigating threats?
11:49 am
Ukraine specialises in PhP programming, has lax laws and a population hungry to earn.
Russians specialise in servers. Look on freelancer websites to determine specialities.
China has a lot of cheap labour, Triads and a lot of black market economy money and makes the items for sale.
Personally, I think this is the new reality because Brexit, Middle East conflict etc. leaves a huge population who are anti 'rules' and keen to do anything to make money. For example - the Somali pirates a few years ago was a symptom of the USA/UK/Germany dumping medical and radioactive waste in their fishing waters, killing their food source. So piracy syndicates earned money to 'compensate'. You can't expect people to just sit there and take it. Given the ease, anonymity and low risk of computing based 'revenge' (Versus bank robbery) I am sure you can foretell the future.
The one I worry about is the Swift banking system. Parts run on OS2 and the ATM's on XP.Can't update because of risk and can't run a trial version to test, so the banks sit in fear. Only a spelling mistake saved them from a multi billion loss in India last year. How long before the hackers succeed?
12:00 pm
Offshore attacks mean legal protections and headaches for those who have been victimized, Dean. It would be quite difficult for the US to get somebody in China extradited for trial. Nor would a victim have much luck recovering damages in a civil suit.
12:14 pm
Just speculating now, but I see to immediate factors that can explain that.
1. Most people don't engage in cyber crime if you can have a well paid job with the skills you've got. This is easier in the US and other rich countries than in other countries.
2. US is probably the preferred target, considering market size and language. This counts for every hacker in the world. If, just for the sake of the discussion, the US would have the same number of hackers per capita as the rest of the world, it would still only count for about 4% of the world's hackers since it only has about 4% of the world's population.
12:15 pm
*two
12:15 pm
We perform regular red-team exercises on ourselves where we pretend to be hackers and essentially hack ourselves. We also perform regular scans and audits to protect our own infrastructure. And we also delete as much data as we can so that there simply isn't anything interesting to go after if someone attacked us.
I think malicious actors are world-wide, the USA isn't immune. However I do think there are higher concentrations in some geographic areas.
Mark.
2:51 pm
AFAIK greed knows no bounds. And it isn't really related to "oppressed people."
Just for example, consider the criminals taking down all kinds of high end sites, through massive DDOS attacks. Attacks so huge, security expert Schneier stated they must be by state-level actors. https://krebsonsecurity.com/2016/09/the-democratization-of-censorship/
Not at all, in fact. Turns out all of this is done by teenage college students with lots of skill and no moral compass. https://krebsonsecurity.com/2017/01/who-is-anna-senpai-the-mirai-worm-author/#more-37412
11:55 pm
I personally think that if someone tried running a major attack from within the US, they would eventually get prosecuted to the full extent of the Federal/State law. I would also speculate that bullet proof hosts are much more difficult to find in the US, compared to some less developed countries.
So even if you tried running an attack network from within the US, then either 1) your hosting provider would pull the plug on you and close your accounts, or 2) you'd get a court order. I'm guessing that most people that engage in illegal activity from within the US, use servers that are out of US jurisdiction.
10:38 am
Is there no method to legally go after hosting providers like "PP SKS-LUGAN" who seem to be clearly hosting malicious sites, to take down the provider itself, under some law or other against illegal activities or knowingly hosting the same (ignoring legit inquiries / notifications that sites they're hosting are engaged in illegal activities)?
Seems like one should be going after the source(s). If they're in the "criminal activity" or "shielding / accessory to criminal activity" business, surely there is some method to shut them down and/or prosecute them?
Just wondering...
I'm sure laws in different countries differ, and folks probably make use of haven countries where laws are more lax or haven't kept up with technological advances... But, surely, there must be some way to cut things off at the source?
11:59 am
In some countries, Police have not been paid for months. When paid, it's $30 a month. The elites rape the economy doing side deals. So, the population finds ways to get a pay increase using the same tactics as the rich. Every one for themselves.
Philippines - head of justice in the senate arrested for funding and running a drug cartel.
So the poor man gets creative.
The whole 'system' gets in on the corruption and you have your answer.
12:13 pm
Hi MG,
As the old internet shorthand goes: IANAL (I am not a lawyer) and international cyber law is a complex topic. Our area of expertise is protecting the WordPress community and our Premium customers. So we try to focus on that and we share threat intelligence with the larger community where we can.
Mark.
10:39 pm
I'm curious is it possible just to blacklist (i.e. drop) this provider network segment on the internet backbone level.
5:15 am
That IP space has been already blocked some time ago by Spamhaus:
https://www.spamhaus.org/sbl/query/SBL190623
So you can use their service not to route this traffic, or just add the spammer IP pool to you Wordfence advanced blocking setting.
10:41 am
The new JerseyShore: Gym, Tan, Money-Laundering.
Thanks for sharing Mark! You guys have the coolest jobs around; this is all very fascinating to learn about.
12:12 pm
Thanks Kyle. I wish I had a tan. Seattle doesn't have much sun! ;-)
10:46 am
This is such great detective work. Thanks for watching out for all the rest of us.
12:12 pm
Thanks Marie. Glad you enjoyed it!!
Mark.
10:47 am
Have you reported these findings to the FBI?
12:05 pm
The cost of these attacks are borne by the general population so there is no 'reward or pay cheque' from protecting the population. Budgets are stretched to pay for 'higher priorities' and cyber security of your blog isn't on the list. FBI and others are busy promoting regime change for their paymasters, not protecting you, they are protecting the government and promoting the Government's priorities.
Sorry, but you are on your own and that's why you need Wordfence! :)
12:11 pm
Hi Dave,
We don't currently report individual attacks. As I mentioned to another poster, we work with other industry partners to help protect the online community although we don't currently share threat data. The industry is moving towards getting better at threat sharing with standards like TAXII and STIX, but it's not quite there yet.
The idea is to not just share a single threat actor, but to provide an ongoing feed of threat intelligence to partners to help them better protect their customers or community.
Mark.
10:47 am
Nice write up. Looks like you're using Maltego. Do you have any recommendations on how to do that style of analysis?
12:10 pm
Hi Chris,
Yes Maltego is one of our tools. I would say it's valuable but not an end in itself. It's also really up to how good the analyst is who uses the tool. Maltego is great but it has some serious limitations in some areas. We use Maltego XL which is not cheap (about $2k per license) so that we can bring in more data. We work with a variety of other tools to try to get a complete picture of the threat landscape and to perform individual investigations like these.
Mark.
10:52 am
Great work WordFence! Are there plans to get direct involvement with government officials to speed up the process at catching these criminals?
12:07 pm
No plans currently although we have friends in government and a few of our team members have worked in government cyber security. There's an ongoing dialogue in our industry between government and private sector on how to better share threat intelligence e.g. which IPs are doing the hacking at any instant in time. The entire industry is working to improve threat sharing with standards like TAXII ad STIX. We have, for example, recently had a meeting with two major vendors in which we shared threat intelligence that helped one of them improve their firewall rules.
So the whole industry is really working towards doing a better job of protecting the online community.
Mark.
10:55 am
So, are the attackers inserting pages into legitimate WP websites that brings a user to their site in order to purchase the counterfeit goods?
12:02 pm
Often it's simply to have the search engines index that page and pass on pagerank to the counterfeit site they're trying to promote.
Mark.
11:06 am
Would I be in the wrong to suggest the American Government apply targeted sanctions against these recipients?
Passing this data on to the relevant government entities is hard. Who would we try to contact? Gary Cohn? Grace Koh?
12:02 pm
I'm not sure that would help. You might target a company or ISP and they would just change the name on the door and peer with other providers. It's a tough challenge. I don't want to see a regulated Internet, and so I'm not in favor of putting up borders in cyberspace. I think the way we're tackling the issue now is quite effective. We develop threat intelligence that allows us to put firewall rules in place to tightly target these threat actors and their TTPs and in this way we very effectively protect our customers (and our free community users too).
Mark.
11:07 am
Thanks so much guys! Up to now I have just test-driven the free wordfence product on my test staging site, but info like this shows you guys really actually care. It's enough to make me consider using your premium product on my production site as well.
Loved the detail in your organization report. Keep up the good work!
12:00 pm
Thanks James. We have some amazing analysts working for us and Rob is definitely one of them.
Mark.
11:09 am
This is first rate analysis folks. Very very impressive stuff!
11:59 am
Thanks Rupert!
11:12 am
Thanks for this in depth analysis of these attacks. I have spent the week scrubbing 5 sites from a 1 page static HTML to a Joomla 2.5 site. Of course three Wordpress sites were in there. I always recommend your plugin first when it comes to a Wordpress site. Any chance you guys will develop a Joomla plugin?
11:59 am
Hi Dwayne,
No plans currently for a Joomla plugin. WordPress is really our 'wheelhouse'. For now. :)
Mark.
11:26 am
Thank you so much for this article. My blog was hacked exactly as described. Last year I didn't really work on my blog, leaving it vulnerable as I did not keep up with wordpress/theme/plugin updates so I suspect that's how they found a way in mid-January 2017.
What finally tipped me off to look into it was I did a search from Google images by typing in my domain name. There were images of sports apparel linking from my site and redirecting to a sales page. Also, they created a directory under my public_html entitled "homefeatured" where all the images were housed and redirection scripts.
Since then, I have installed the free version of Wordfence and monitor daily, took extra steps with regards to Cloudbleed - and as soon as I have the funds, I will be upgrading to the premium version of Wordfence to block certain countries as that's what I'm noticing the influx of attacks are coming from (and they are still trying to access those apparel pages).
Thank you Wordfence for these informative updates and a great product!
11:58 am
Thanks for the kind feedback Cristina, glad to hear we helped.
Mark.
11:33 am
Good article. Is there any possible way to stop these attacks ?
12:19 pm
Yes. Install Wordfence. Even the free version blocks all attacks from this campaign.
Mark.
3:09 pm
Thank you mark, we get hit at least 300 times per week, one night, it was over 800 attempted attacks....NOPE...Wordfence kept the Goulies out .
Larry...
DieppaLaw.Com
5:04 pm
This is an extremely well written article, as are all of the blogs you post. I am not only referring to the use of simple, clear and concise language to explain complex IT information but the grammar is superb. It's not something I normally experience from so-called computer 'nerds' but each exposé is like an exciting and enthralling detective novel, which could be the basis for a must-see TV program. I'm waiting for the sex, drugs and rock'n'roll to be included in the next blog!
By the way, we deal a lot with China, with transactions paid through Western Union and recently we had these transactions queried by Western Union. I wondered at the time what it was all about but your explanation about the money trail seems to be a good reason for their diligence in checking that everything is legit.
Keep up the good work wordfence team.
6:00 pm
Thanks Bill. Much of the credit for grammar and style goes to Dan Moen, my colleague who edits man of the posts (and also contributes research etc). I'm still figuring out the difference between "its" and "it's" - my fingers seem to have memorized the wrong one for each occasion.
Mark.
5:12 pm
Eye opening! I heard about someone's site that got hacked and that prompted me to take action and I have installed Wordfence on my site and I am so glad I did after reading this article. This should be taken up on a high level with the Chinese authorities and get them to crack down on the hacking as well as the counterfeiting! Hopefully the publicity from this when it goes viral online will prompt action on the Chinese end. Thanks, Mark.
6:01 pm
Thanks Irene.
7:09 pm
Good article, interesting read. We have seen this across our servers as well with actually a very large surge in the last 12 hours. Our ban list from mod_sec has grown more in the last 12 hours than in the last 15 days!
9:44 pm
Thank You WordFence.!!
You really have a great Team!
9:52 pm
We have noticed an unusual number of hits to WordPress login pages the past month or two.
After reading this article I did a scan of our log files and found IPs in the 91.200.12 rang in the logs for many of the sites we host.
Your post was very informative. Thanks!
10:18 pm
Nice job laying out the investigation tactics
11:10 pm
Fascinating! Huge thanks Mark and team for sharing your knowledge and insights about current security issues. It is an amazing privilege to have Wordfence protecting my site AND also get access to your very well-written, up-to-date information!
11:21 pm
Thank you for your extended sharing of information. It is really good that you decided to come fourth with actual hostnames, IPs, providers etc. It means you value your work!
Thank you for your great plugin for WP. It's being a valuable tool to the security of our systems.
12:31 am
Very impressive and interesting article Mark! Thanks for the precious info.
-oliver
12:52 am
Dear Mark,
Congrats, great job. I have to say that I found your posts very informative. As an agency that sells wordpress websites you may understand how important for us is to offer security for our customers. So, thanks again for your efforts. Best regards from Italy!
1:16 am
Interesting Article, Thanks Mark for sharing info about their tactics.
3:34 am
I can't claim to really understand this, but I am very glad that you do.
Keeping one step ahead of the problem makes you super heros!
Thank you for educating us.
4:15 am
Guys - has it occurred to you that you have moved into a realm of significant international criminal activity and the possible consequences of this? I ask only because I am beginning to fear for your personal safety!
7:05 am
Thanks for being so awesome guys and providing such great protection and updates.
Mike
10:57 am
You guys are amazing!
As I former web developer and of course a proud WF users I can't emphasize on the importance of having a plug in like Wordfence.
Thanks for all of this information and hard work. Keep up the fantastic work, we are in good hands!
11:12 am
Thanks Astrid.
11:53 am
This is a fantastic post. I really appreciate what you all are doing and especially enjoy reading articles like this which point out the forensic work you're doing. A fantastic read!!
As an aside, I took on a client w/ an out-dated, non-updated WP site who wanted to a redesign/rebuild. It got hacked right after I took over, but Word Fence's scan tool rescued me. I was able to save the site w/o grep'ing through the entire site to run down the malicious code. In fact, it was a similar type of operation (selling "Cuban" cigars rather than sports jerseys).
Ever since then, I won't install a WP site w/o Word Fence. Look forward to the days of bigger clients whom I might sell the premium version :)
Keep up the great work and the informative posts!! They're inspiring me to learn more CLI networking too!
-J
12:40 pm
Thanks James!
4:58 pm
You guys are absolutely amazing. No organization like this out there for WP site admins. Thank you so much!
11:00 am
I sleep much better at night with Wordfence in place.
Your "live traffic" feature showed I was getting about 6 attempted hacks every 20 minutes. Wait, WHAT?!
Thank you for what you do -- I quite happily plunked down the dollars to buy your premium protection and recommend it to all my WP blogging friends.
3:01 am
I notice on the wordfence information that it lists all the attempted admin logins blocked as well as the successful logins when I login myself. If a hacker did get in, they would see the successful login to use wouldn't they under that section? Can this section be blocked to hackers who do get in?
2:04 pm
You can't block anything to a hacker who 'gets in'. Once your site has been compromised, all bets are off.
12:00 pm
I've noticed quite a number of these attacks recently, and recently had to counter spam registrations. Thank you for all that you do to keep my site safe! This information is much appreciated.