WordPress-Delivered Ransomware and Hacked Linux Distributions
In a rather unfortunate turn of events earlier this month, the Hollywood Presbyterian Medical Center was infected with ransomware. Ransomware, if you’re unfamiliar with it, encrypts everything on your workstation and then tells you to pay an attacker to decrypt your system and regain access to your information.
In the case of Presbyterian, they had to pay 40 bitcoins or the equivalent of $17,000 to regain access to their systems. The ransomware attack affected CT scans, documentation, lab work, pharmacy functions and their email went down. Last week they paid the attacker the $17,000 and their systems were decrypted and they’re back online.
Unfortunately WordPress has been a source of ransomware infections. It’s unknown whether it contributed to the Presbyterian attack or not. During the past month the information security industry has seen WordPress used as a kind of platform to launch ransomware attacks. It works as follows:
- A WordPress site is hacked through any method available. That may be a brute force password guessing attack or by exploiting a vulnerability in a plugin, theme or core.
- The attacker installs code on the WordPress site that redirects visitors to other infected websites that are running the Nuclear Exploit Kit. The redirects may happen through a series of websites to try and prevent web browsers and Google from warning you that a site is infected. The sites involved in the redirect change frequently.
- When a visitor to the infected site is redirected, the nuclear exploit kit searches for vulnerabilities in the site visitor’s Flash Plugin, Microsoft Silverlight, Adobe Reader or Internet Explorer.
- If Nuclear finds a vulnerability, it exploits the visitor machine and installs the TeslaCrypt Ransomware.
- The ransomware then encrypts all files on the workstation and extorts the owner into paying to get their system decrypted.
This is what TeslaCrypt looks like:
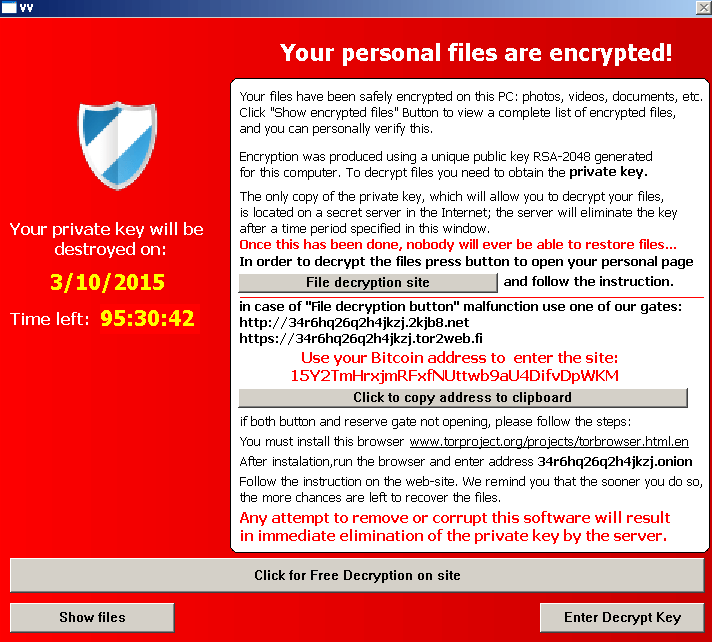
A screenshot of the screen that TeslaCrypt displays when your files are encrypted. Courtesy Bromium Labs.
As you can tell from the sequence of events above, TeslaCrypt and the attackers behind it rely on a cascade of failures. They require multiple vulnerable WordPress sites to perform their infection and to set up a chain of redirects. They then need a visitor using an unpatched workstation with vulnerable applications to visit an infected site.
The fact that Hollywood Presbyterian actually paid the ransom to regain access to their systems, speaks volumes about how effective a ransomware attack is and the impact it has on systems.
Update: If you are infected with TeslaCrypt, there is a utility available written by an anonymous researcher called TeslaCrack which may help. Thanks to Samuel who posted it in the comments below, where you can find a link to the utility along with a few other links I’ve added discussing the utility.
In another turn of events, the Linux distribution “Mint” reported on Saturday that they had their website hacked via a WordPress installation. According to Clement Lefebvre, the project leader, in reply to a comment on their blog:
“We found an uploaded php backdoor in the theme directory of a wordpress installation, which was 1 day old and had no plugins running. The theme was new but most importantly I think we had lax file permissions on this. This was only set up hours before the attack but we were probably scanned for something like this for a while. Anyhow, we don’t know yet how it was uploaded but we know it happened there, and I’m certainly not pointing the finger at anybody. People just asked if we were running wordpress or if wordpress was used in the attack and I answered yes.”
The attacker replaced the real Linux distribution that Mint users download from the site with a version that had malware installed. The modified Linux distribution turns your Linux machine into a member of an attack botnet that can be used for DDoS attacks.
As WordPress site owners, our role in this is clear. If you don’t protect your WordPress site from attackers, you risk infecting your site visitors with Ransomware, turning their machines into an attack platform, or worse.
When thinking about WordPress security, it’s important to consider the broader impact a hack might have, and the larger responsibility that we as site admins have to not just protect our own website and our investment, but our site members’ personally identifiable data and the security of visitors to our websites.
At Wordfence, we continue to provide detailed advice on how to keep your WordPress site secure including here on our blog and in our WordPress Security Learning Center. Securing your site is critically important, not just to protect your investment, but for your site visitors’ safety.
In other news: We’d like to remind all ElegantThemes customers to update their themes if they haven’t already. There was a critical security update released on Thursday that fixed a vulnerability in several of their themes. Update immediately if you haven’t done so already.
As always we welcome your comments below. Please share this with the larger community to create awareness of our larger responsibility as WordPress site administrators.

Comments
9:44 am
I think you need to change the title of this article to "WordPress-delivered" instead of "WordPress Delivered." I read the subject in my email that you just sent and thought you were saying that WordPress delivered malware and hacked ISOs.
10:16 am
Ditto! I panicked - thinking that the trusted Wordpress Foundation was directly delivering Wordpress.org distributions that were laced with ransomware back-doors.
D:
Good to know. Thank you.
10:26 am
Dangit, I replied to Will as soon as he posted but ended up replying on a different blog post. Thanks Will, I made the change immediately when you posted your comment. We're not in the habit of posting click-baity titles, so hope it's clearer now.
9:51 am
Thank you for sharing such interesting wordpress security updates.
9:53 am
What puzzles me about a ransomware attack is when you pay the money it must go to someone, a company, a person. Why can't the police find these people?
10:51 am
Bitcoins are the closest financial transactions can get to being anonymous right now - and if you could discover the culprit, chances are, he's located in a country that doesn't extradite for computer hacking.
11:13 am
So, couldn't one just delete all their files through FTP, delete the database and create the site again from scratch? I don't understand how this works. What am I missing? Is this only a problem if you don't make regular backups?
11:38 am
Yes, that is correct. This can affect personal and business computers, not just websites, and unfortunately many people don't make regular backups.
11:47 am
The encryption is of files on you computer, like photos and documents. Fixing your web site may prevent the site from being used to infect others but does not unencrypt the files on the computer.
6:53 pm
If you do have a backup, you will most likely be safe. I was infected a while back as I tried to download drivers from a shady site. As soon as I discovered that some files were encrypted, I panicked. But quickly I hunted down the software on my PC, removed it completely, restored a backup of my data and send the guy a "screw you".
11:37 am
Based on the screenshot and what I've read elsewhere, payment is required in Bitcoin, which has no direct connection to anyone's real world identity, and associated communications are via Tor, which runs over multiple encrypted proxies, preventing a network trace. Finding the culprits is not impossible, but is pretty close unless you have NSA-level resources.
Even if you did manage to track them down, the hackers who commit these types of crimes can be located anywhere in the world – and if they're smart, they target victims in other countries. If you live in, say, Miami, and you go to your local police with a ransomware attack, even if you got lucky and somehow tracked down the culprit, when they see it's coming out of China or Uzbekistan or something, there's just not going to be much they can do for you.
12:20 pm
We have an excellent resource that explains Tor in the learning center: https://www.wordfence.com/learn/the-tor-network-faq/
Bitcoin can be anonymous. Bitcoin has a kind of public ledger in the blockchain that gives you public knowledge of all transactions and transaction history. All transactions can be traced to a wallet, but if you can't tie the wallet to an identity, you can't figure out who the individual is. Any individual can create as many wallets as they'd like - some recommend creating a new wallet for each transaction.
12:22 pm
The Police in the Ukraine, China, or Brazil (the biggest Hacker countries) are useless for resolving complaints. In many cases the hackers either work with or are protected by the authorities.
10:16 am
Surely the Hollywood Presbyterian Medical Center had back-ups that they could have reinstalled?
4:04 pm
Good point. We were hit with ransomware last year, but not via Wordpress. We were hiring staff and I inadvertently opened a macro enabled word doc titles resume and BOOM! It started to encrypt the main SBS in addition to my machine. I powered down the server and my machine and restored from the previous evening's backup. My machine was a wipe the hdd and start again scenario, but we lost half a days trading data across the business group.
Moral of this story is back up and back up often even if it's only incremental. And then make sure you have multiple copies of backups offsite and regularly check that you can restore something from a file. If something like this happens, take a copy of the most recent backup out of circulation until your sure that your out of danger. Like a month. It saved my bacon as I had to restore a few bits and pieces over the following week that was missed.
Portable hdd are cheap and having multiple offsite backups which are rotated gives you a near foolproof disaster recovery. Oh and run in a VM environment. These days if you are running a business server for small to medium businesses and you're not doing so as a VM, you're completely insane. Site burns down, you take the backup of the entire server environment to a datacentre, mount it on another hyperisor. Back in business within a day or two at worst.
6:35 pm
Neville,
I am in total agreement with you, someone should lose their jobs over this.
I have no less than three backups of every data I own, and websites included. Both securely cloud stored and physically on my premise in an extremely secure SAN. The entire annual cost is <$150.
5:48 am
We here in the technical trenches know how easy it *should* be to do backups, and how obvious it *should* be to do them.
That said, I read somewhere else that this event was likely the result of outsourcing IT in order to save money. I hope this is a lesson learned that the last place to cut your budget is in IT in such a high-stakes environment.
10:39 am
Wow, now that is friggin' scary! =S If there was ever a top reason to secure your site as much as possible, this is definitely a story worth sharing! Thanks guys! =)
10:44 am
Those ransomwares can really be a hard thing to deal with. I faced TeslaCrypt 1 month ago. One of my client got infected by this ransomeware. The process was tricky but I made my way out and wrote an article on how I did it. Here is the link [Editor: To the utility he used to clean his site. I'm assuming you're not the author. Thanks for the info Samuel.]: https://github.com/googulator/teslacrack
10:58 am
Looks like this tool may be effective at cracking teslacrypt. More on the Norton forums about it including several replies from the author: http://community.norton.com/en/forums/how-decrypt-teslacrypt-vvv-files
More press on this utility here (Credit for the utility is incorrectly attributed to a vendor. It's developed by an independent developer.): http://www.myce.com/news/indian-security-researchers-crack-encryption-of-teslacrypt-ransomware-victims-get-files-back-for-free-78399/
If you have been hit by TeslaCrypt, this may be a solution until the malware is updated to fix the flaw TeslaCrack is exploiting.
11:25 am
TeslaCrypt has MANY variants. The older variants indeed can be decrypted using TeslaCrack by Googulator or TeslaDecoder by BloodDolly. These include the ones that leave files with the extensions .ecc, .exx, .ezz, .abc, .aaa, .xyz, .zzz, .ccc, and .vvv. However, the newest variants have corrected the flaw, and it is no longer decryptable. The newest TeslaCrypt 3.0 uses the extensions .xxx, .ttt, .micro, and .mp3.
[Editor: Removed marketing links]
9:56 am
Thanks for the credit, Mark.
11:04 am
Thanks Mark for the information.
Jeffery Frankel, Bitcoin is quite difficult trace. Bitcoin was built to be anonymous but sometimes it can be tracked if the user makes a mistake somewhere in their process. Additionally, most police departments haven't got a clue but since this is Los Angeles bothe the LAPD and LA County Sheriff's department are big enough to have "Cyber" divisions so you can be sure one of them are working on this case.
Neville Gosling,
You would be amazed how many large, corporate and government offices DON'T have a backup plan or routine. I am stunned to see just how many BIG companies don't have a plan and their only recourse to the CryptoLocker, RansomWare type attacks, is simply to pay up. Otherwise you simply format, reload your OS and move on and suffer the loss of data and hope it's just not that bad.
Good Luck to everyone!
-Root-
11:37 am
I am not questioning this scenario, but sometimes I do wonder if it's just easy to blame WordPress.
That aside, will people ever learn that backups are often the most important function they can perform to help themselves?
Off my soapbox.
11:47 am
Again thanks for a great insight but in addition to good security you should also have a good backup routine in place which in turn could get rid of the problem easily. As long as you can work out how your site got infected in the first place
But I think this post high lights something much more important and that is the duty of care that we as site owners have towards our visitors in ensureing their visits to us are safe.
11:54 am
Here's a story about a school district in South Carolina (Myrtle Beach) that's paying the ransom. Here's one of the stories: http://www.myrtlebeachonline.com/news/local/education/article61869482.html
1:48 pm
I have both WordPress security and wordfence installed, I keep my plugins up to date and yet, my website gets compromised on average every 2 weeks... Maybe I'd be better without any plugins..
2:24 pm
I think the responsibility of linux or server is hosting providers. We have to trust them. Am I right?
11:14 pm
Yes you are right, the linux operating system, apache and any other software that's crucial to server doing it's job is our responsibility, however, the software and scripts, eg wordpress, plugins and themes that you put on the server are your responsibility. It works both ways my friend.
4:22 pm
I watched once as a folder in my DropBox suddenly got attacked by ransomware. I was getting a ton of notifications on my screen that something was happening and fortunately it was a folder that I rarely used, but it was accessed by some people who must have had low security systems. It was kind of creepy to watch files get converted to some file format I never heard of. I was able to delete that folder immediately from DropBox and that ended the threat. I did get to see their ransom message. Sheesh.
7:14 am
It's worrying that paying the ransom seems to have become a precedent. I was at a cyber crime insurance presentation today (UK) and you can get cover for ransomware attacks, including ransom payout if deemed necessary. This short-term approach seems likely to create more TeslaCrypt variants and more hackers.
9:55 am
Interesting Andrew, thanks for sharing. I suspect ransomware might become very popular in the next decade because the business model is now proven.
3:17 am
Wonder if the host can provide any security at all? A regular backup and some strict rules to work with should keep you safe.