Announcing 3 New Login Security Features
Spend any time looking at blocked attacks in Wordfence Live Traffic and you’ll walk away worried about login security. WordPress sites are under constant attack by bots attempting to guess your users’ passwords. A lot of these attacks simply test lists of commonly used passwords along with usernames they think you may have chosen, like ‘admin’ or different takes on your domain name.
More recently we’ve started to see more sophisticated attackers leveraging lists of passwords from data breaches in their attacks. These are referred to as credential stuffing attacks and have a much higher success rate than traditional password guessing attacks. If you’ve given other users access to your website, are you confident that they haven’t reused their password? If they have, you may be just one data breach away from a hacked website.
Today, with the release of Wordfence 7.3.1, we are excited to announce several new login security features! They are:
- A completely rebuilt two-factor authentication feature, now available in the free version of Wordfence
- Login page CAPTCHA
- Improved XML-RPC protection
Together with the other login security features already included in Wordfence, these additions give you robust, layered protection from password guessing and credential stuffing attacks.
Completely Rebuilt Two-Factor Authentication Feature
Two-factor authentication, or 2FA, adds a second layer of security to your users’ accounts. It requires them to not only enter their password, but also a second piece of information only they have access to. An account protected by 2FA is virtually impossible to compromise. Even if an attacker discovers your username and password somehow, they still can’t log in.
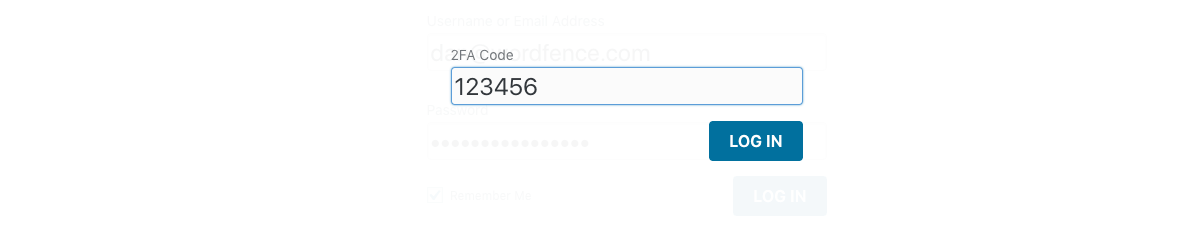
Use Any TOTP-Based Authenticator App
The new Wordfence 2FA feature leverages authenticator applications and services that support the time-based one-time password (TOTP) standard. There are many of them to choose from on the market; Google Authenticator, Authy, FreeOTP and 1Password are just a few. Many of you are probably already using one of these. For those who aren’t, they are incredibly easy to set up and use.
Wordfence 2FA is Now Available For Free
2FA is now available for use on sites running both the free and Premium versions of Wordfence. When we first added 2FA to Wordfence roughly 6 years ago, we leveraged SMS to send you a text message with a 2FA code when logging in to your site. Since sending SMS messages costs money we made it a Premium-only feature. A couple years ago we added an authenticator app option in addition to SMS.
The previous iteration of our 2FA feature is now being phased out completely and the replacement no longer includes an SMS option. Sites with the old version activated are able to continue to use it, but are strongly encouraged to transition to the new one. SMS is a less secure way to deliver login codes and is prone to delivery issues. In fact, NIST now specifically recommends against using SMS-based authentication.
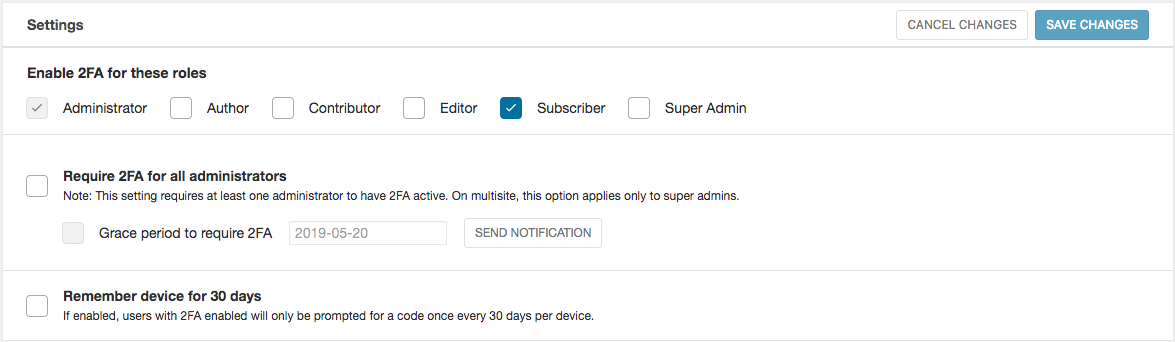
Enable 2FA For Any User Role You Want
While it’s most important to protect your site’s admin accounts, there are plenty of other user roles with capabilities you don’t want to hand over to an attacker. Wordfence now lets you enable 2FA for any role you like. Simply visit the Settings tab on the Login Security page within Wordfence. Sites with the old 2FA version enabled will need to migrate to the new version before they see the Login Security menu link. A notice at the top of the old 2FA page in Tools will invite you to migrate to the new version of the feature.
Whitelisted IPs That Bypass 2FA
This field accepts IP addresses or ranges where 2FA will not be required. You can use this to skip 2FA on networks you trust, like if you have a static IP. Another example is if you have a network with a trusted range of IPs, such as allowing users on your corporate network to log in without 2FA unless they are logging in from outside the network.
New Login Page CAPTCHA Feature
In recent years the number of IoT devices has exploded. Unfortunately they have been highly prone to security vulnerabilities. This has resulted in a massive increase in the size of botnets available for attackers. In the context of login security for WordPress, this means that attackers have more compromised machines, and IPs, to use in their attacks. By spreading attacks across much larger pools of IP addresses they are able to dial the number of login attempts made by each IP address down so far that they evade even the most aggressive login attempt limiting rules, at least at the site level.
Earlier in the year we experienced an attack just like that, where the attacker was leveraging hundreds of thousands of IP addresses in a very sophisticated manner. We determined that in order to effectively thwart the attack our best option would have been to deploy CAPTCHA protection on our login page, effectively nullifying the attack.
As is often the case, a solution to a problem we’re facing with WordPress security becomes a great product idea. You are now able to enable Google reCAPTCHA v3 on your login and registration pages using Wordfence. It does a fantastic job of blocking bots from attempting to log in while allowing humans through without incident.
As a fail-safe, any user that Google erroneously deems to be a bot (and who does not have 2FA active) may continue logging in by clicking a verification link in an email sent to the account’s email address. User registration attempts that are blocked may also send an email to the email address configured for site administration, which is rate limited to prevent abuse.
Improved XML-RPC Protection
XML-RPC is an interface that allows WordPress to communicate with other applications. It is unfortunately often overlooked by WordPress users when discussing login security. “Just move your login page and you’re secure!” they say with bravado. Unfortunately they are often wrong. In the last 30 days, 60.6% of the login attempts blocked by Wordfence were hitting XML-RPC, not the site’s login page.
Fortunately there is a way to secure XML-RPC as well, with the new login security features in Wordfence.
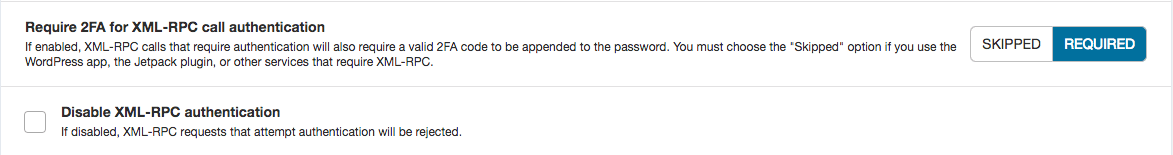
Disabling XML-RPC
Because XML-RPC is such a popular target for attackers, we strongly recommend that you figure out whether you need it or not. If you do, protect it with 2FA if possible. If you don’t use the WordPress app or the Jetpack plugin it is likely safe for you to disable XML-RPC.
If you don’t need it, disable it. Once you know it is safe to do so, disabling it is as easy as checking a box in your Wordfence settings. Just be aware that it may cause you problems in the future should you start using an app or plugin that requires it.
Two-Factor Authentication for XML-RPC
If you have a custom application that logs in via XML-RPC, it can be configured to append a TOTP code when logging in using Wordfence. This option allows you to protect your XML-RPC endpoint from brute force attacks while making it available for your custom app. Unfortunately most off-the-shelf plugins and apps that utilize XML-RPC cannot be configured to use 2FA just yet, but with Wordfence you’ll be ready for when they can.
Conclusion
In this age of massive botnets and constant data breaches, login security has become increasingly important. These new features combined with our existing ones will provide you with the tools you need to implement the layered security approach that will keep your site safe. We strongly recommend that you upgrade to the latest version of Wordfence if you haven’t done so already, and invest the time to enable these powerful new features.
Thanks and stay safe!



Comments
12:08 pm
Does 2fa work for frontend theme login as well?
12:25 pm
It should work fine in some cases, but there is good chance the theme developer’s code will break the 2FA code popup. In most cases users can still log in by appending their 2FA code to their password (pw+code).
12:14 pm
I would like to use this Plugin to solve a serious problem. DimenXional not only has its own Cloud products but we resell for other suppliers. One supplier in particular has not secured the "Create an Account" or the "User Login" to what I would consider to be industry standards. In fact, on the 12th we have a Bot attack that resulted in over 750 bogus accounts in WordPress because of this failure by this extremely well known industry supplier.
The problem is they supply multiple URL's that the user must use to login to the account we have sold them. The authentication clearly impacts our user tables in WordPress, otherwise we would not have had a problem on the 12th.
What is required to be able to use this plugin but redirect the customer to their account that is not on our servers? I am guessing it must be some type of PHP program. Has Wordfense given this problem any thought?
12:41 pm
I'm not completely following what you're trying to do, but if the users are being created and logging in via a second system (not your WordPress site) it is unlikely that it will work.
12:20 pm
This is by far the most exciting news recently,
Thanks
12:32 pm
Great article about the advanced security measure for Login. I like the Captcha idea but the article does not mention how to enable it. I looked in my Wordfence section, but do not see the where this can be enabled.
12:38 pm
Hi Fred, you can find the Login CAPTCHA feature under Wordfence > Login Security > Settings. It's the last option on the settings page titled "Enable reCAPTCHA on the login and user registration pages".
12:38 pm
A would love to be able to turn off xml rpc to everything apart from Jetpack
12:42 pm
Interesting idea, we'll discuss internally. Thanks Peter!
1:34 am
That'd be very useful indeed! +1 from me.
7:05 pm
I agree.
12:50 pm
Great news that you made 2FA available to the free version. Keep up the good work!
12:54 pm
This is a great news! I will uninstall third part two factor authentication and start to use your amazing think.
I will suggest (maybe also on Wordpress support forum) to add ReCaptcha protection also for comments not only to login page because for example i am using a plugin that create conflict with the new two factor auth introduced by Wordfence. The plugin that cause issue is Invisible reCaptcha for WordPress. For security will be nice if also comments on website can be protected by the ReCaptcha managed by Wordfence.
Thank you again, amazing!
1:46 pm
Excellent features, you are awesome! Please note next time where those features are and how they can be turned on. =)
They are under Tools.
2:21 pm
Hi Joseph, in Wordfence 7.3.1 there is a new Login Security link in the menu, that is where all of these new features are found.
3:55 pm
Dan:
You wrote: Hi Joseph, in Wordfence 7.3.1 there is a new Login Security link in the menu, that is where all of these new features are found.
I have the legacy WF 2FA using Google authenticator not SMS. I dont see the new "login Security link".. Do I need to activate the new 2FA to see all of the new settings? Also, my site has only one user only whom is an administrator. Am I correct since using legacy I simply need to hit migrate vs switching and all is well? Do I need to cancel the current google authenticator info (delete) in wordfence since not SMS based but authenticator based? Dont want to get locked out for any reasons...
4:13 pm
You should see a notice at the top of the old 2FA page in Tools inviting you to migrate to the new version of the feature. You should not need to remove and set up your authenticator app users. If you're worried about potentially getting locked out we recommend logging in with another browser or an incognito window before you start the transition.
4:30 pm
Excellent, thank you
11:06 pm
First, thanks for the plugin. It is extremely useful in helping me stay on top of site security.
Can I just check that I have understood the effect of implementing 2FA? I'm not a security expert, so I may not have.
If you are a single user with sensible passwords, it makes no practical difference to brute force attacks. It adds another 20 bits of randomness, but if your password already has 60 bits or more, that makes no practical difference. (It is true that an attacker cannot do an exhaustive search even in principle, but they can't do that in practice even without 2FA.) It might help if the attacker has the password hash file, and there is a vulnerability in the hash algorithm that they can exploit, but that strikes me as a very low risk. (That depends on whether an attacker with that information could generate recovery codes. I assume not, but I don't know how this works.) (Further note: if you have multiple users, it forces them to have at least 20 bits of randomness in their passwords, and thus blocks brute force attacks against them as well. That is definitely a benefit.)
It essentially blocks sniffing attacks by making them into brute force attacks.
It protects against phishing attacks, for the same reason.
It is no use against pure social engineering, because that involves convincing the user to log in for the attacker, and the user needs to be able to log in. It does make it very hard to steal credentials for later use in this way, however.
Are there any major effects I have overlooked?
I live in an earthquake zone, so I also have a use-case in which all my devices are destroyed or inaccessible, and I need to be able to access the website to let people know I am safe and communicate to sort out what to do next. At the moment, I can do that as long as there is a publicly accessible internet machine, and provision of those seems to be a fairly high post-disaster priority. With 2FA, I get locked out. Thus, I have to balance the risks, and to do that I need to understand them.
Sorry about the basic questions, and thanks for any clarification you are willing to offer.
8:33 am
Hi David, the impact of enabling 2FA with a TOTP-based authenticator app is very different than simply increasing the length of your password. The six digit 2FA code changes every 30 seconds, so even in the case of a successful phishing attack they would need to make use of the stolen credentials in real time. You can read more about the TOTP algorithm here: https://en.wikipedia.org/wiki/Time-based_One-time_Password_algorithm. Regarding the emergency scenario you outlined, during activation you are encouraged to download onetime use recovery codes. Printing them and storing them in a secure location would work assuming they weren't destroyed or made inaccessible as a result of the hypothetical disaster.
1:40 am
I can't find the XML-RPC and reCapcha settings in WordFence central. Are the not in there and will they be added?
9:45 am
We're working on that. Please note that some of the options will not be available in templates.
1:45 am
We have recently seen many log-in attacks using real first names of our employees or ex-employees as wordpress user name. Seems hackers actively search LinkedIn to find user's first names that they try to log on with.