The January 2017 WordPress Attack Activity Report
Last month we introduced a monthly attack activity report. This report gives you an indication of attack trends during the past month and how they have changed. Today we are releasing the January WordPress attack activity report which covers the period from January 1st until January 31st.
Most Active IPs
In the table below we have listed the most active attack IPs for January 2017. Note that the ‘Attacks’ column is in millions and is the total of all attacks that originated from each IP. Further right in the table (you may have to scroll right) we break out the attacks into ‘brute force’ attacks and ‘complex’ attacks.
Brute force attacks are login guessing attacks. What we refer to as ‘complex’ attacks are attacks that were blocked by a rule in the Wordfence firewall.
We have also included the netblock owner which is the organization, usually a company, that owns the block of IP addresses that the attack IP belongs to. You can Google the name of the owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for their IP, so this is not reliable data but we include it for interest. For example, we have seen PTR records that claim the IP is a Tor exit node, but it is clearly not based on traffic.
We also include the country and a country flag. To the far right of the report we show the date in January we started logging attacks and the date attacks stopped. For many of these IPs we logged attacks for the entire month. For some you can see there is a clearly defined attack ‘window’ where the IP started and stopped.
The first interesting thing about our January attack data is that the same Ukraine IP holds the number one spot this January as we saw in December. Our top 3 attacking IPs all appeared in last month’s list.
However, only 5 of the attacking IP addresses in this month’s top 25 also appeared in last month’s top 25 list. This is an illustration of how the IP addresses that attackers use are rotated out and new ones are used to launch attacks.
The Seychelles attacker we saw last month has dropped off the list. In addition, we have Turkey appearing on the list for the first time with three IP addresses hosted at “Yalcin Kanbur trading as Webrano Hosting”, generating over 6 million attacks during January between them.
India has also appeared on the list for the first time with an IP hosted at “Reliance Communications” generating around 2 million attacks during January.
A Change in Complex Attacks vs Brute Force
Last month we saw 66.7 million brute force attacks and 63.9 million complex attacks from our top 25 attacking IPs. You’ll recall that a complex attack is one that targets a plugin, theme or core vulnerability and is blocked by the Wordfence firewall.
This month we’re seeing 64.1 million brute force attacks from our top 25 attacking IPs. However, this time around we’re only seeing 34.5 million complex attacks.
This change indicates that the most prolific attackers have changed their strategy and are focusing more on brute force WordPress attacks than on trying to exploit vulnerabilities in WordPress core, themes and plugins.
Brute Force Attacks on WordPress in January 2017
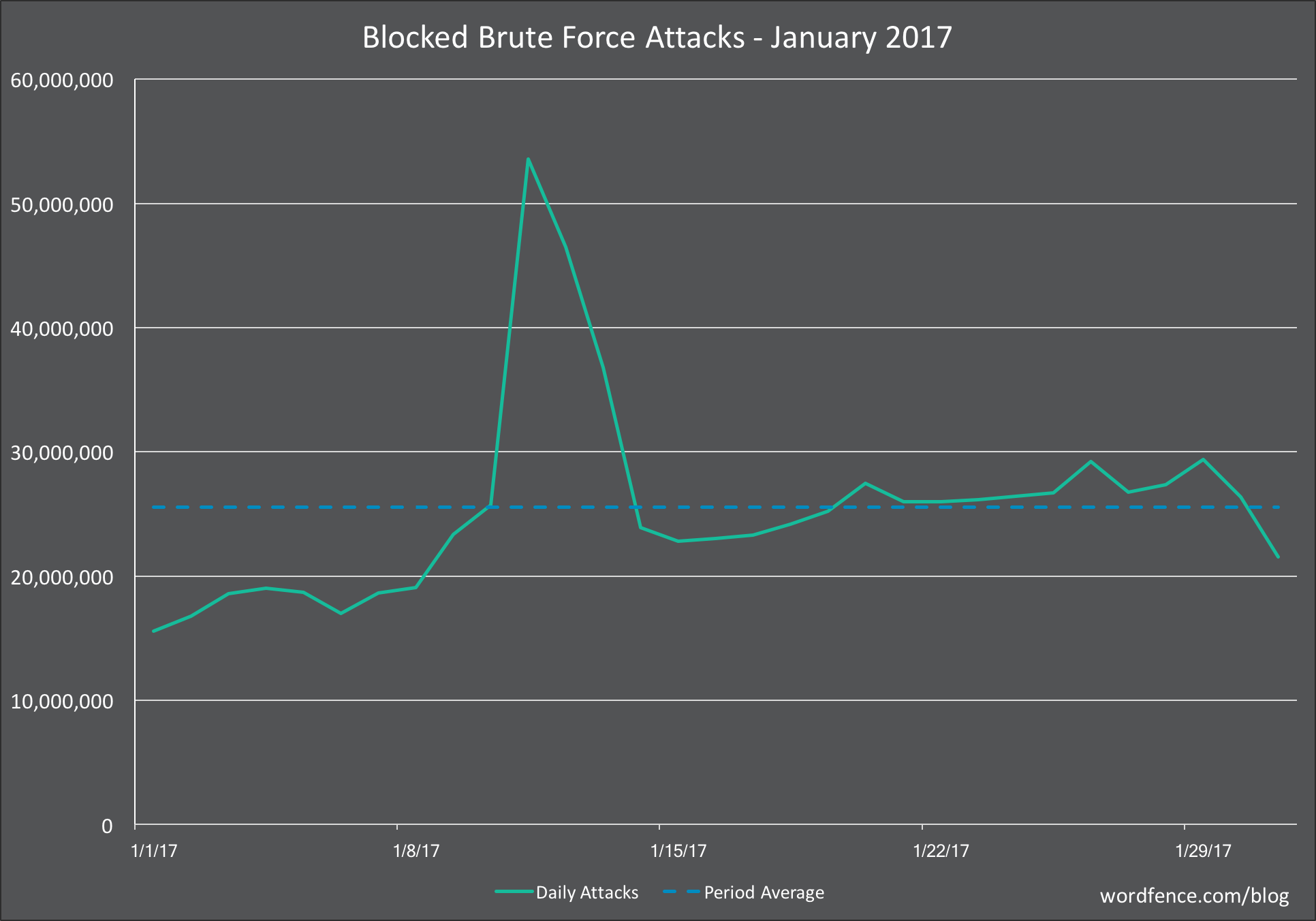
The chart above shows the brute force activity on WordPress sites that we saw in January. You’ll notice a huge spike in activity just before the middle of the month. This really gives you an idea of the kind of volatility that can occur.
We will occasionally see situations like this where an attacker will gain access to servers that they can use as an attack platform. They will generate a huge amount of activity until their IPs are shut down by the hosting provider or network admin.
In December we saw a similar spike but it only peaked at about 46 million attacks per day. In January the peak was approximately 53 million attacks per day.
This contributed to an increase in the average attacks per day for January which was 26 million attacks per day compered to 20 million for December.
Complex Attacks on WordPress in January 2017
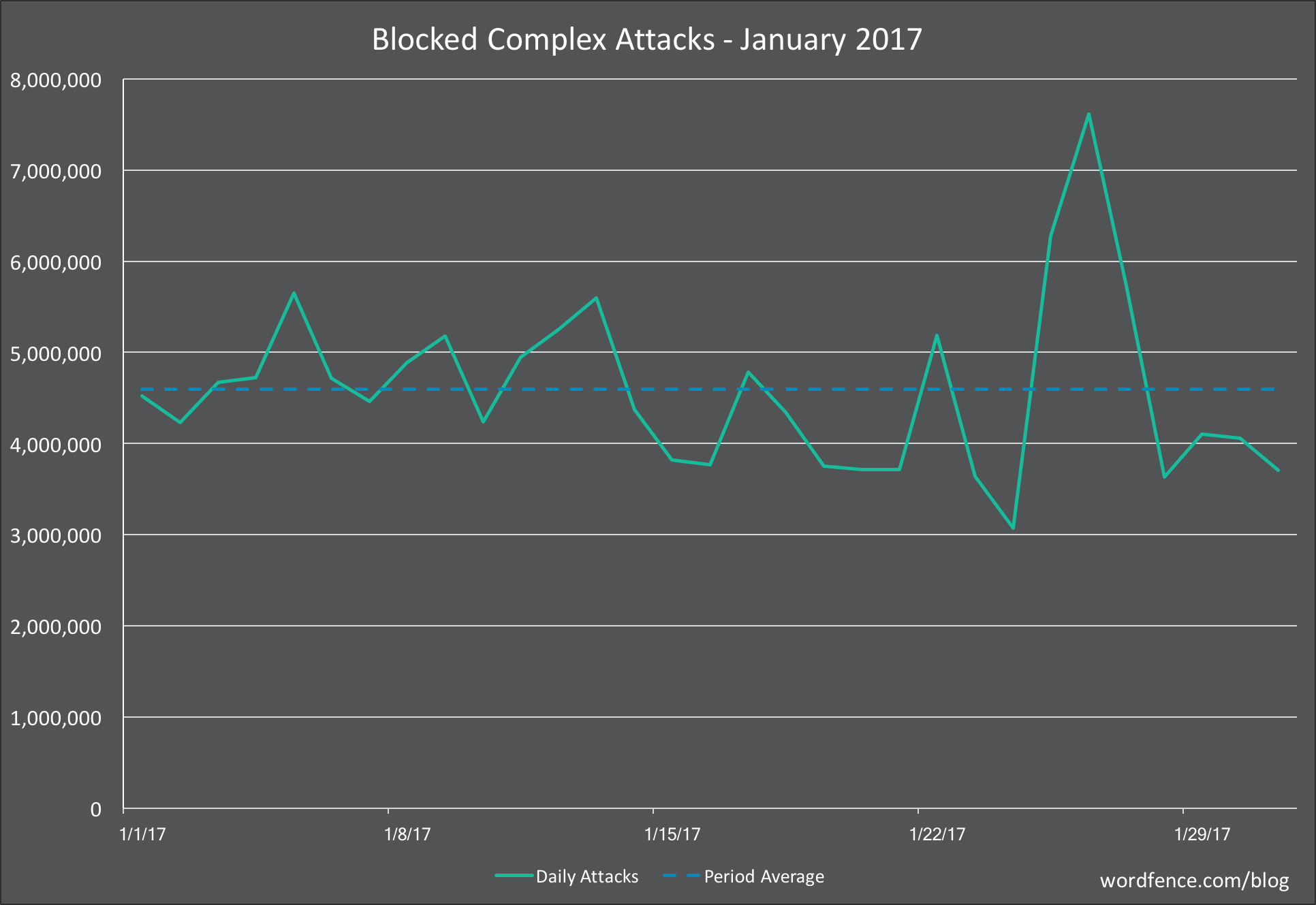
We saw a decrease in attacks on the Wordfence firewall in January 2017. The average number of attacks dropped from 5 million attacks per day in December to 4.7 million attacks per day in January.
This decrease in the number of attacks is due to only a single large spike in attack traffic in January compared to a sustained spike in December that lasted more than 1 week.
However the number of attacks in January during the low periods was significantly higher than in December with 3.5 million in December compared to 4 million at the lowest activity in January.
Attacks on Plugins
The table above shows the top 25 plugins that experienced the most attacks during January 2017. The table shows the rank in January, and then the change in ranking compared to December. If you scroll to the far right you can see the number of attacks per plugin during the period.
The WP-Mobile-Detector plugin saw the biggest gain in the number of attacks, jumping 25 points in our rankings to position 12. The plugin has been removed from the WordPress plugin repository, probably because a vulnerability was not fixed by the author, and the last review was posted over 7 months ago.
The plugin continues to see attacks, which may indicate that some WordPress sites still have this installed and are still vulnerable. It may also simply be because attack toolkits that attempt to exploit multiple vulnerabilities incorporate this exploit and then throw a series of exploits at websites in the hope that one of them works.
Let me know in the comments if you have any additional data you’d like to contribute that may indicate reasons for plugin gains or losses in number of attacks, or any other insight you’d like to share.
Attacks on Themes
The table above shows attacks we saw on themes in January and we’ve included the change in ranking since December. The rankings for these themes are incredibly stable. The largest change we saw is “linenity” which has a local file inclusion or LFI vulnerability that became public knowledge back in April 2014. The vulnerability allows an attacker to download the wp-config.php file.
The stability of the rankings in theme attacks suggests that there is not much innovation among attackers targeting themes for attack. They are likely using the same old attack toolkits that try to exploit the same old theme vulnerabilities and the rankings stay stable as the attack toolkits remain relatively unchanged.
Attacks by Country
In this report for the first time, we are including data on the number of attacks originating in each country. Because this is a new addition to our monthly attack activity report, we won’t have ranking change data for this month.
The number of attacks below are the sum of brute force and complex attacks that originate in each country. It’s important to note that this does not indicate that a specific country’s government is launching attacks. Instead this is a general indication of the state of security in each country.
There are a few factors that may cause an increase in attacks from a particular country:
- The country simply has a large number of servers hosted within it’s borders. This is likely the case with the United States which has the most servers hosted within it’s borders out of any other nation.
- The country may have a lack of enforcement when complaints are received. In other words, if local law enforcement is lax, there may be malicious hosting providers within the country that are able to act as attack platforms.
- There may simply be a large hosting provider within the country that has a security problem and is inadvertently providing an attack platform via compromised servers for the rest of the world.
Conclusion
That concludes our first Wordfence Attack Activity Report of 2017. As always we welcome you to download the data in the tables above to perform your own analysis and share it here in the comments.
Please post any questions or feedback in the comments and as always I will be around to try to answer them.
Regards,
Mark Maunder – Wordfence Founder/CEO.
Special thanks to Dan Moen and other Wordfence team members who produced this report and who also tirelessly manage the code and infrastructure that enables us to provide this insight to the community.

Comments
9:12 am
Thanks for all the hard work you folks do! I really appreciate your transparency.
9:13 am
Thanks Morgan!
9:15 am
As always nice to see the work behind the software, I've a couple of points that I think are note worthy!, the first is that as wordpress reveals the username of the user that made a post brute force attacks are always going to be high on the agenda untill word press (or Wordfence ) allows us to obscure the posters name in some way, the second is that we also see majorly high numbers of "Russian" and "French" attacks however we've examined the host and providers and find that the "French" ones are mostly from phoneytelecom (renown for providing tunnels!, and the "Russian" attacks also come as a one off ip (hit and run) suggesting a proxy server with anonymous access is being used each time we also saw many hits from "tor" end points nationality of which we can't comment.
All in all I'd guess the country I'd that's being used isn't as effective as you think but that's just from my own reasearch of the attacking ips
9:17 am
Thank you for good work on this. You are appreciated very much.
9:45 am
Thanks a lot, my data show different list of countries, but in substance is the same. Someone noticed an end of attacks around a couple of days ago ? my sites are passed from 1 k attempt login daily to few ones.
Specially my second site, hardly attacked from months, have peace.
Thanks again for the hard work, not only to protect our sites but also to inform us.
10:58 am
You guys are amazing!
I was wondering, though... since it seems that your plugin is awesome! And I rely on it heavily for my site securty, are you concerned about hackers ganging up on you? You must be their worst enemy now, surely. :)
Love your work!
12:35 pm
We've never experienced that. I don't think they're that interested in us.
11:53 am
Many thanks to you, Mark and team, for your continued excellent efforts. Very much appreciated!!!
12:17 pm
I second what Danny said above. Security is HARD.
12:27 pm
There has been many blocking attempts against login attempts. Word fence automatically blocks. Question is, that does it do any good to permanently block that which Wordfence has temperately blocked?
12:35 pm
I wouldn't recommend that Paul. IP addresses change and non-hackers end up using blocked IP's. So you probably want to just block temporarily and if they misbehave again they'll be blocked again.
Mark.
10:31 am
Re Paul's question above, If a network is assigned a range of IP addresses, and that network is in a country where most of your attacks originate, Russia or Ukraine for instance, then if you permanently block that IP would it follow that if it gets reassigned it will only be to another in that same network? I don't care if anyone from those countries ever visits most of the website I manage because they don't target audience from there, so the more blocks I have the better it seems to me - or am I missing something?
Thanks again for these blog posts!
5:32 pm
Thank you for your sharing of information and thank you for the awesome plugin...
6:09 pm
I am diffinatally sharing this report. I want others to see how often WP is being attacked. Maybe people will think twice before using WP as a site builder. Had I know this, I would not have built my site with WP and am now in the process of changing builders.
WP should be creating their own plugin's and NOT relying on 3rd party players.
Maybe before changing from a blog publisher to a site builder some more thought and brainstorming should have been done.
And again, don't tell us about the attacking IP' s... tell the FBI CyberCrime unit and ICANN.
8:01 am
Greg, I don't think this kind of attack traffic is unique to WordPress. You are just hearing about WordPress on this site because it is the platform WordFence works with. I manage sites on WordPress, as well as other platforms and they all see a significant amount of attack traffic.
You can help protect yourself where plugins are concerned by making sure that the plugins you add are regularly maintained, have an active and helpful support team, and keeping your plugins and WordPress core up-to-date.
10:18 pm
Thanks Mark for your effort. Keep it up. ;)
6:59 am
Have been using your plug-in on a few sites and have believe it is the best plug-in for protecting our sites here in Australia, having said that the fact that you are keeping us all safe and up to date in this day and age of the www being such a hostile environment for small business especially, I thank you for all your time and effort.
In the near future I shall upgrade to the Premium version as country blocking would be an advantage to our sites when analyzing traffic etc and also less attacks, one would hope.
Great work, Kudos to you and your team.
7:19 am
I, for one, would be very happy if you just blocked the Ukraine permanently. No one there has any use for any of my sites or probably any other sites in the west. If Ukranians woke up one day to find that they couldn't access the outside world, they would protest loudly and then the government might step in to investigate. At least block the country long enough for it to make some noise.
12:34 pm
There is a shooting war on in Ukraine. So jurisdictions aren't clear, enforcement isn't a priority.
10:20 am
Having been once hacked I'm so grateful for Wordfence!
Re Adam's comment above, doesn't using a nickname different from your username and choosing it to be displayed publicly in your profile take care of that?
Also, I've noticed attacks on themeify ramping up lately on the sites I manage.
9:57 am
I'd also like the answer to Eveline's question ... can the username be hidden without resorting to fiddling with the database (or anything else technically dangerous)?
2:11 pm
Just joining the many above. Thanks for the work you do. I'm new to WordFence. But, it has done wonders for increasing security on one of my sites that had experienced several hacks.
10:22 am
I've been thinking about the attacks we're seeing on all sites, and reading various blogs and comments from the last couple of years. Many of the attacks we're seeing are targeting usernames which are not the common ones ... my own for example is not a name, word or IT-related phrase - I doubt anyone else uses it anywhere.
Because the hackers can discover my username from WordPress (because it is inherently insecure), my username has become the target of brute force attacks.
They are never going to get in that way because of my password ... but it's a load on the server ... and when many sites on a server are being constantly attacked, it affects performance.
WordPress need to address this so the username is in no way identifiable.