The December 2016 WordPress Attack Activity Report
This week we are introducing something new. At the beginning of each month we will be doing a monthly WordPress security report. We will look at the attack data for the previous month from the 1st to the end of the month and provide a report and analysis on the attack activity we have seen on WordPress websites.
This is the monthly WordPress attack report from December 1st, 2016 until December 31st, 2016.
Most Active IPs
In the table below we have listed the most active attack IPs for December 2016. Note that the ‘Attacks’ column is in millions and is the total of all attacks that originated from each IP. Further right in the table (you may have to scroll) we break out the attacks into ‘brute force’ attacks and ‘complex’ attacks.
Brute force attacks are login guessing attacks. What we refer to as ‘complex’ attacks are attacks that were blocked by a rule in the Wordfence firewall.
We have also included the netblock owner which is the organization, usually a company, that owns the block of IP addresses that the attack IP belongs to. You can Google the name of the owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for their IP, so this is not reliable data but we include it for interest. For example, we have seen PTR records that claim the IP is a Tor exit node, but it is clearly not based on traffic.
We also include the country and a country flag. To the far right of the report we show the date in December we started logging attacks and the date attacks stopped. For many of these IPs we logged attacks for the entire month. For some you can see there is a clearly defined attack ‘window’ where the IP started and stopped.
The data below is embedded using a service called Airtable. This is the first time we’re trying Airtable, so please leave your feedback in the comments. You’ll note that it is also exportable.
Ukraine still owns the top spot
As you can tell from the table above, the Ukraine absolutely dominates the report. We have a total of 13 out of 25 top IPs that are based in Ukraine. Attacks are originating from 4 Ukrainian netblock owners:
- PE Tetyana Mysyk
- Pp Sks-lugan
- Kyivstar GSM
- ISP Datasvit network
Surprisingly, France takes the number 2 spot for the most IPs in the top 25 list with a total of 7 attack IPs. Most of these originate from Iliad Enterprises. Iliad is a large organization with many subsidiaries and over 4000 employees. They tried to buy T-Mobile in the USA 2 years ago. The netblock for these IPs is registered to Iliad, but the attacks may originate from one of many subsidiaries of Iliad, like the ISP ‘Free’ in France.
Seychelles
The outlier on the map is an IP address “89.248.172.121” based in Seychelles, which is an island off the east coast of Africa. Seychelles has a population of just over 90,000 and is officially the smallest sovereign African nation.
We logged 2.2 million complex attacks originating in Seychelles. This is surprising because internet access to islands is generally expensive and slow. But Seychelles is doing their part to contribute to global attacks on WordPress publishers.
We tracked the attacks to what appears to be an audio-visual store in downtown Victoria in Seychelles, based on public whois information for this IP. The IP is not a known Tor exit node and it probably is not a VPN exit node because it is unlikely that Seychelles has their own VPN provider.
Based on usage patterns we are seeing available in public data (try a Google search), the IP appears to be the public IP for users of a local Seychelles ISP. The attacks are probably an individual based in Victoria, Seychelles, who is using the ISP.
Complex Attacks vs Brute Force Attacks
A brute force attack is a password guessing attack that is simplistic and has a low likelihood of success. At Wordfence we consider a ‘complex’ attack to be an attack that tries to exploit a vulnerability in WordPress or a WordPress plugin. If you are using Wordfence to protect your WordPress website, brute force attacks are blocked by our brute-force protection and complex attacks are blocked by the Wordfence firewall.
The top two IPs, one in Ukraine and one in Russia, are both using complex attacks to target WordPress websites. They are also launching far more attacks than the top brute force attacker. They launched 32 and 12 million attacks respectively, while the top brute force attacker only launched 6.3 million attacks.
However, if you look at the total attacks we saw for the top 25 IP addresses, we saw 63 million complex attacks and 67 million brute force attacks. The most active IPs are choosing to launch complex attacks that are blocked by the Wordfence firewall, but the most common attack type is brute force, or password guessing.
This makes sense because more sophisticated attackers will launch a high volume of attacks that will have a high success rate. They will therefore choose to launch complex attacks and a huge number of them. Less sophisticated attackers will launch brute force attacks but won’t be able to deliver the same attack volume as the pros. So you should see a lot of lower volume IPs engaging in brute force attacks and a few high volume IPs engaging in complex attacks, and that’s exactly what we are seeing.
What, no Tor?
Something that we noticed in this report that we did not include in the table is the number of Tor exit nodes in the top 25 attack IPs. There are none. In our full dataset, we can see a large number of Tor exit nodes. We identify them from a list of Tor exit nodes and in every single case, both complex and brute-force attacks originate from the exit node.
In the top 25 list, not a single IP is a Tor exit node. Tor exit nodes are probably used by several low volume attackers for a wide variety of attacks. Using Tor is anonymous, but slow. Tor introduces a lot of latency (delay) in web requests. When you decide to bulk hack millions of WordPress websites, you probably don’t want the latency that comes with using Tor. You can learn more about Tor in our Learning Center.
Brute Force Attacks
If you recall our post on December 16th where we described a “Huge Increase in brute force attacks in December“, we saw a marked increase in the number of attacked sites starting in late November. We also saw the number of attacks gradually increase above our 60 day average, peaking at just over 2o million attacks per day. And finally around the 16th of December was saw a dramatic spike in the number of attack IPs engaging in brute force attacks. Reference the original brute force post for those charts.
Now that we have the full data for December, you can see that this culminated in a huge increase in total attacks at the end of the month.
In late December we saw a massive spike in brute force attacks. The average for the month was 20 million attacks per day, and the total attacks we blocked spiked to over 45 million for a period of 48 hours.
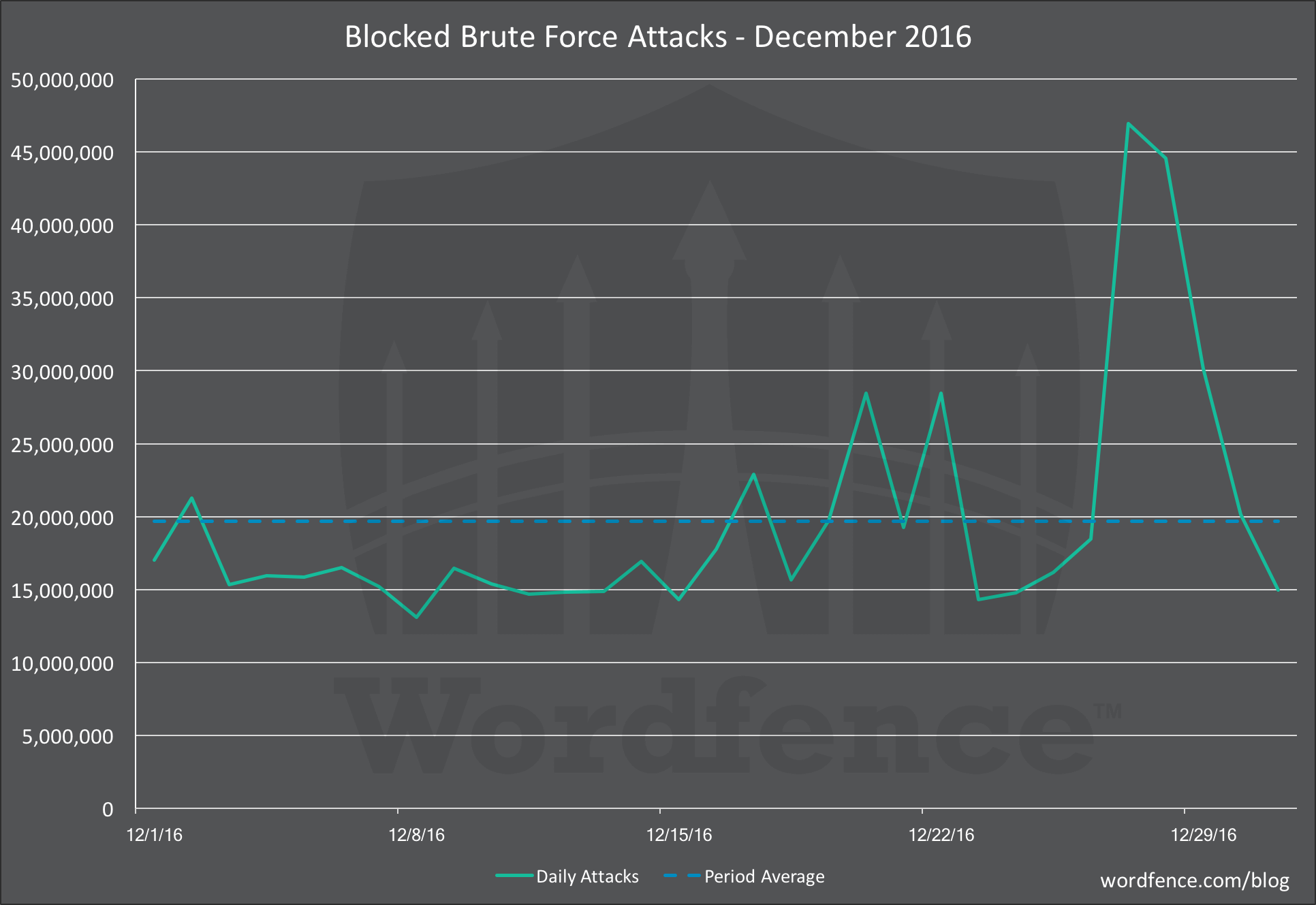
As you can tell from our top 25 data, no single IP generated more than 6.3 million brute force attacks for the entire period. To add an additional 25 million attacks per day, over and above what we normally see, an attacker would have to compromise a large number of IP addresses and then launch attacks distributed across their new attack platform. The data from our mid-month report showed that large spike in new attack IPs.
The attack quickly died down and this may have been due to the noise the attacking IPs were generating. It would have been easy for hosting providers to detect outgoing malicious activity on their networks and shut down the servers that were launching these attacks.
Early this month we have seen brief spikes of similar activity that have lasted a few hours. We have not yet seen a multi-day effort like we saw in late December.
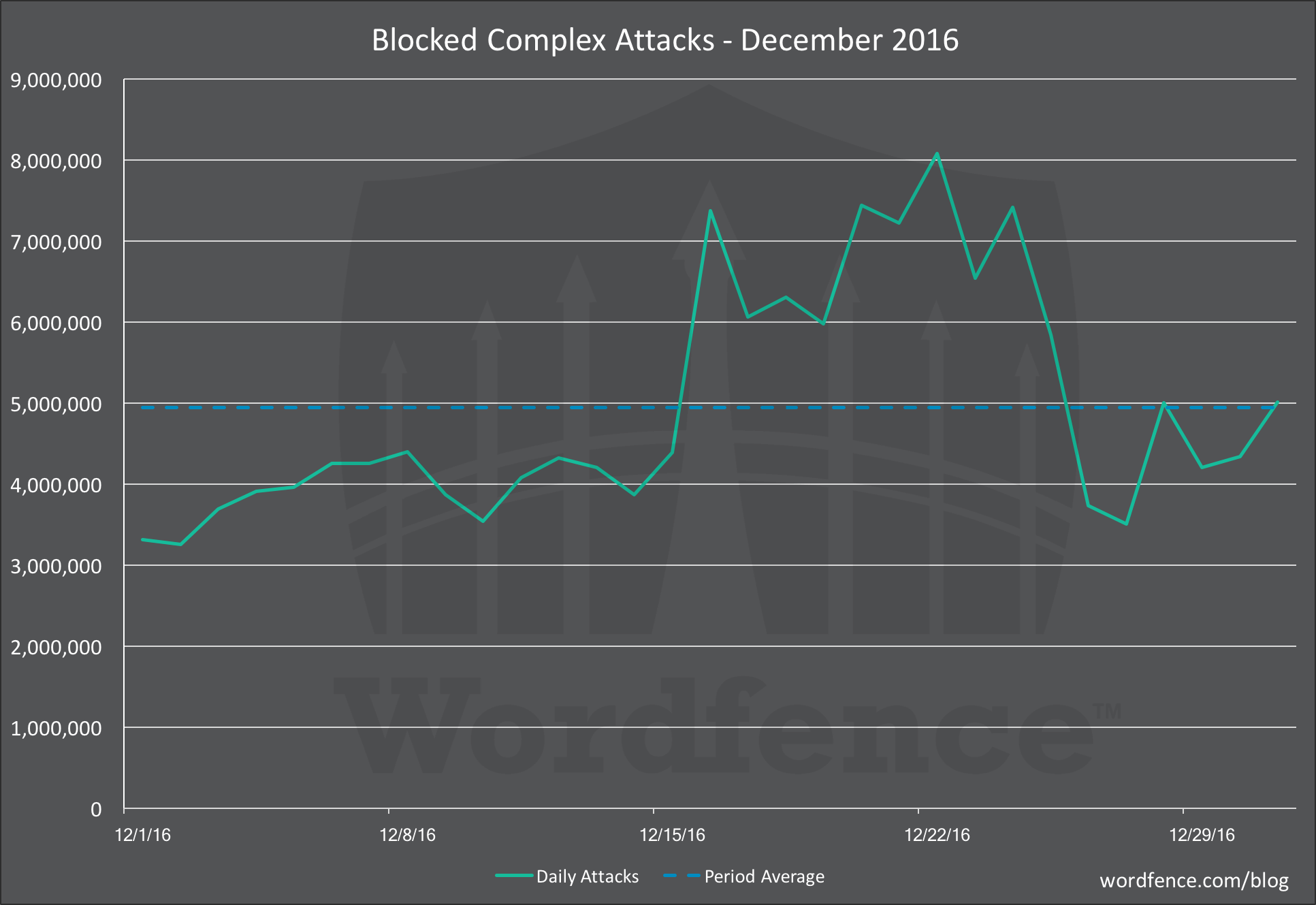
Complex Attacks
From December 15th to December 27th we saw a marked increase in complex attacks that were blocked by the Wordfence firewall. Attack volume did not quite double, as we saw in the brute force chart above.
The peak attack volume for complex attacks blocked by Wordfence was just over 8 million attacks per day. There is no strong correlation in the timing of complex attacks and brute force attacks or the duration. They appear to be disconnected.
Plugins seeing the most attacks
The table below shows which plugins were most targeted by attacks in December 2016. You should note that all of these are publicly known vulnerabilities that the plugin vendor is probably aware of and has fixed, although we have not verified this.
The list below is simply a list of what we are seeing attacked in the wild. It is not a list of “most vulnerable” plugins or a list of plugins that are currently vulnerable.
The “Plugin Slug” is the unique ‘slug’ used to identify the plugin to WordPress. It is easier for us to extract plugins by ‘slug’ from our attack data than get actual plugin names.
Each plugin has a link to a vulnerability report that is likely the vulnerability being exploited in each case. (Click the slug) We have also included the year the vulnerability was published next to the slug.
You’ll notice that many of these are old vulnerabilities. Some of them date as far back as 2012. The reason we think these old vulnerabilities are being so widely exploited is because most attacks use free, off-the-shelf WordPress scan and exploit tools.
These tools come pre-loaded with a number of exploits that an inexperienced attacker can automatically launch at any WordPress website. This makes up the bulk of the attacks on WordPress plugins that we see. They have a low likelihood of success if you are keeping your WordPress installation up-to-date.
| Rank | Plugin Slug | Attacks Blocked |
| 1 | google-mp3-audio-player (2014) | 3,866,201 |
| 2 | db-backup (2014) | 3,607,072 |
| 3 | wp-symposium (2015) | 1,635,894 |
| 4 | dzs-zoomsounds (2015) | 1,617,512 |
| 5 | really-simple-guest-post (2015) | 1,230,015 |
| 6 | wp-ecommerce-shop-styling (2015) | 1,123,328 |
| 7 | candidate-application-form (2015) | 1,117,750 |
| 8 | tinymce-thumbnail-gallery (2012) | 1,043,966 |
| 9 | pica-photo-gallery (2012) | 1,023,009 |
| 10 | plugin-newsletter (2012) | 1,011,422 |
| 11 | simple-download-button-shortcode (2012) | 986,659 |
| 12 | dukapress (2014) | 946,831 |
| 13 | wp-filemanager (2013) | 909,217 |
| 14 | jquery-html5-file-upload (2016) | 883,365 |
| 15 | recent-backups (2015) | 847,996 |
| 16 | simple-ads-manager (2015) | 825,505 |
| 17 | wpshop (2015) | 775,787 |
| 18 | aviary-image-editor-add-on-for-gravity-forms (2015) | 774,018 |
| 19 | acf-frontend-display (2015) | 771,248 |
| 20 | formcraft (2016) | 764,899 |
| 21 | work-the-flow-file-upload (2015) | 757,809 |
| 22 | woocommerce-product-options (2016) | 757,531 |
| 23 | wptf-image-gallery (2015) | 752,382 |
| 24 | inboundio-marketing (2015) | 751,198 |
| 25 | front-end-upload (2012) | 745,027 |
Themes seeing the most attacks
The list below shows the slugs of themes that we saw most commonly targeted in December 2016. Once again, this is not a list of vulnerable themes or the ‘most unsafe’ themes. They are simply commonly targeted and most likely had vulnerabilities at some point that have now been fixed.
We’ve included the year each vulnerability that is being exploited was published and most of the slugs in the table have links to the exploit that is most likely being used.
As with the plugins, this list contains many old exploits, probably for the same reason. Most of the vulnerabilities in this list are “local file inclusion” vulnerabilities that allow an attacker to download wp-config.php or other sensitive files.
| Rank | Theme Slug | Attacks |
| 1 | mTheme-Unus (2015) | 3,485,508 |
| 2 | churchope (2014) | 3,399,433 |
| 3 | lote27 (2014) | 2,566,892 |
| 4 | elegance (2014) | 1,840,865 |
| 5 | awake (2016) | 1,838,267 |
| 6 | infocus (2014) | 1,830,555 |
| 7 | echelon (2014) | 1,386,527 |
| 8 | dejavu (possibly 2014) | 1,310,259 |
| 9 | construct (unknown) | 1,155,775 |
| 10 | fusion (2015) | 1,147,655 |
| 11 | persuasion (2013) | 1,128,816 |
| 12 | method (unknown) | 1,110,563 |
| 13 | myriad (unknown) | 1,099,149 |
| 14 | infocus2 (2015) | 1,096,006 |
| 15 | parallelus-mingle (unknown) | 1,084,646 |
| 16 | trinity (2014) | 1,083,314 |
| 17 | urbancity (2014) | 1,081,411 |
| 18 | epic (2014) | 1,078,927 |
| 19 | parallelus-salutation (2015) | 1,067,890 |
| 20 | modular (unknown) | 1,067,402 |
| 21 | linenity (2014) | 1,063,945 |
| 22 | authentic (2014) | 1,043,639 |
| 23 | antioch (2014) | 981,204 |
| 24 | NativeChurch (2015) | 891,350 |
| 25 | estrutura-basica (2015) | 451,997 |
Conclusion
That concludes our monthly attack report for December 2016. You are welcome to download the top 25 list of IP addresses and perform your own analysis. The Airtable embed includes an option for a CSV download.
We welcome to share your own findings in the comments and any questions you might have.
Mark Maunder – Wordfence Founder/CEO.

Comments
9:21 am
Thank you, Mark, for taking the time to make this report.
9:21 am
Thanks to the great developers at Wordfence we have been able to select and block large groups of hackers by ip range.
We do business in the US so could care less if we block coutries and regions outside of our domestic area.
The number of brute force and complex attacks have dropped to a trickle.
And the new feature of seeing who and why someone was blocked in live traffic mode is very helpful.
Thanks again for your dedication and effort which allowed us to streamline our defenses.
9:22 am
Excellent & informative article. Understanding patterns and having an awareness of vulnerabilities is the best defence against attackers; that and wordfence ofcourse :).
We are now factoring wordfence premium into our quotations as it is fast becoming an absolute essential for any wp site. Keep up the good work.
9:22 am
Should we block these up addresses?
9:36 am
Wordfence already blocks the attacks that these IP's are engaging in. You can block them outright from within Wordfence if you'd like.
Mark.
12:35 pm
Awesome works guys blocking the IP's. Glad I am paying for premium WF.
1:11 pm
Thanks!
9:23 am
This monthly attack data is going to be a huge help. Thanks for all your hard work and for these news letters.
9:25 am
thanks for the info
9:27 am
Excellent help, thank you. Can I download these IPs and import them into my premium service wordfence plugin?
9:35 am
Yes you're welcome to download the data and use it for anything you'd like.
9:44 am
Awesome report! Can't wait to see more of these.
9:53 am
Once again Mark ( and the rest of the crew) a brilliant idea and so glad i use WF for all my clients sites. I do find it hard telling them how lucky we are and even had a near miss hack if we had not have had WF installed great Job looking forward to the next one
10:01 am
Yet another reason why I LOVE WordFence! Thank you so much for this information! This helps me remain more informed and responsive for our clients to help keep them and their customers better protected!
10:11 am
Hey Mark,
Great work! I'm also experiencing brute force attacks on my website. It started in december. The attacker is using a NetBot so the ip is constantly switching to different ip's all around the world. I noticed it came from the same user agent. So I finally managed to block it using the advanced blocking user agent feature. I'm still being attacked every 30 minutes or so but at least wordfence is now blocking it regardless of the IP or country. I can see the red blocks in my live traffic constantly.
Wordpress is amazing, thank you guys!
Nick
10:13 am
What a cracking job you guys do protecting WordPress sites. I shall use your csv file as source data for my python script to block these IP's at the front door.
Many thanks
10:21 am
Hi Mark,
Great info!!! I'm looking forward to your future monthly reports.
I've been using Wordfence on my clients' sites since it was brand new. It's saved my bacon far more than once!
10:21 am
Great article - I posted to my Facebook page help educate my customers on why they should upgrade to the premium version of Wordfence.
A special thank you to your team in December when they cleaned a very messy attack on four of my client's sites!
1:00 pm
Glad to hear we did a great job. Thanks for the feedback.
Mark.
10:27 am
You guys are awesome. You have NO idea how much your plugin has helped me this past month. I, too have seen Ukraine and France show up on the reports emailed to me.
Thank you, so much for your hard work and dedication!
11:08 am
A thumbs-up from the Netherlands! You are doing great work, keep on going, please... ;)
11:08 am
This is a very welcome feature. Just added the 25 ip's to our firewall's deny list.
Thanks for this!
11:09 am
I have one single question, which, if I could, I would direct directly at the hackers themselves : what are they missing in their lives so badly, that they want to "penetrate" other people's websites like this... maybe they should try to "penetrate" something else instead ?
What a wasteful way to live life on this beautiful planet, trying to harm people's sites that have done nothingn against you. Absolutely wasteful way of living, IMHO.
Good job on catching them !
11:39 am
Thank you, Mark and staff, for demonstrated excellence both in product/service and communicating with customers!
Just curious: As those BFA and Complex Attacks are getting more popular, what is your hunch: Defense/protective measures to become more and more essential, or, a more co-ordinated and sophisticated international law enforcement effort to step in, or both?
Peter
1:02 pm
I think about this quite a bit Peter. I worry that a coordinated law enforcement effort may lead to a much more closed Internet. So I tend to come down on the side of individuals and the private sector doing a better job of securing endpoints. I'd rather not see national firewalls erected that risk creating informational and cultural barriers too.
Mark.
11:39 am
Great report, thank you guys for all the hard work you put in keeping us wordpress managers safe from these hackers. With regard to the airtable - it looks like a great little plugin, and the data was easy to read. It would be cool to be able to sort by various columns though, which doesn't look like an option here (unless you click "view larger version"). Sorting on any column in the embedded version would be a welcome addition to future tables. Keep up the good work!
1:03 pm
OK thanks Drew. I purposely disabled that feature to remove a rather busy header the embedded version had and to also clean it up a bit. I'll add that in the next report and you can let me know what you think.
Mark.
11:48 am
Thank you for all your work and making this information available. The amount of attacks I've been seeing on my websites has been just snowballing in the last few months. Bots were registering fake accounts on one that was a membership site at an alarming rate until I beefed up the sign-up process to exclude them (couldn't acheive this with WordFence free alone). They started out mostly being from Ukraine and Russia, then other eastern European countries. Lately they are coming from everywhere and even Canada and the USA on occasion. Yesterday I found one originating from a network owned by the Worchester Polytechnic Institute in MA that attempted brute force entry to /wp-login.php on an innocent little art site I manage. I had already renamed that page and set options to block anyone attempting to access that url.
Is it likely that the first attacks from eastern Europe succeeded in hacking many sites in far flung reaches and are now launching attacks from those hacked sites?
1:04 pm
Hi Eveline,
That's generally the cycle. Sites will get compromised and get used to further compromise other sites, rinse, repeat.
Mark.
1:25 am
What other Eastern European countries do you see? I don't see any.
11:48 am
Great idea on posting monthly reports! This report is a great way to emphasize how the country blocking premium feature Wordfence has is so useful at times when needed.
1:05 pm
Thanks Mark.
To be honest, I've never liked the idea of blocking countries. We've always tried to provide security on a per-attacker basis. Blocking an entire country creates a kind of nation based barrier to websites. Blocking individual attackers with a rule based firewall like Wordfence seems like a much better approach. But when you have a situation like we have with Ukraine right now, one tends to rethink the approach. It has just gotten out of hand. It's very unfortunate.
Mark.
11:49 am
Thank you very much for this very clear and very useful report. Is this report communicated to private or public organisations specialized in striking cyber crime. Knowing where the problem comes from is interesting but it is essential that some actions be done on the hacking companies.
1:08 pm
Hi Oliver,
We don't share this report or any of our threat intelligence currently with any private or government organizations. Our focus is serving the online community and of course our business focus is sales to individuals and small to medium enterprises (SME's) - that's you guys. We don't do enterprise sales and, honestly, I'd really rather not. We do have impressive threat intelligence and capability these days, but I'd much rather serve and secure the online community than deal with 18 month sales cycles, wearing a suit, and a small number of big customers who can push us around.
Regards,
Mark.
6:29 am
Hi Mark, rest assured that there are plenty of suppliers servicing government organisations that make great use of Wordfence. In fact, that's how I first became aware of it and started using it on my blog - because our national organisations website has it, it was recommended as a necessity since we have a statutory requirement to keep our site going during times of national emergency.
As a security professional, I've always been really impressed by Wordfence and all the great work you do. I recommend it to all WordPress users that I deal with as the first thing to install on a new site.
I wish you all the best for 2017.
12:06 pm
Fabulous and informative report, thanks for doing this. Individual tables, theme and plugin info are all helpful. Thanks for the introduction to Airtable - works great!
Looking forward to your next report!
1:09 pm
Thanks Lisa. Glad it works for you. We get a lot of traffic when we post on this blog, so I wasn't sure they'd be able to keep up, but looks like they handled it just fine.
12:19 pm
Mark
I really appreciate your blogs I find them very insightful.
I look after several websites for small non-profits and genuinely feel comforted by the protection of WordFence. More so because of the blogs you write.
This time I was very interested in the analysis of which plugins have been targeted.
This particular information is very valuable.
Keep up the good work.
Happy New Year
Andrew
1:09 pm
Thanks Andrew.
12:23 pm
Just a correction from my previous comment. Thanks to read "that some actions be done on the owners of the IPs originating from telecom companies " and not "on the hacking companies". Sorry about that.
12:31 pm
This is amazing information but if you already use WordFence then you already know the general countries that attack IP's apparently come from.
It appears to me as a premium and free user that wordpress and or WordFence should block IP's from Russia Ukraine and France as standard, if this was done the ISP's would surely take action to clean up their act.
A bit like sanctions from the world to a country, they are bound to pay attention if they cannot access a large percentage or web properties.
What I find particularly concerning is the growth in IP's that are anonymous (no country identifiable) these are becoming far more common and they are not filtered by country blocking.
I have set all of my premium WordFence sites to block these countries and several more as standard, we cater mainly to local businesses therefore there is no other reason than bad intent for these IP's to be visiting US UK IE and AU sites. If everyone did this then I think that the ISP owners would by necessity have to look at cleaning up their users.
We have one client that we knew had been hacked through Wordpress prior to us taking them on, we monitor this site vigorously, it is being attacked at an astounding rate and WordFence premium is doing it's job, but boy it it getting hit hard! I think once a hack has been successful the URL must be distributed to hack networks, can anyone confirm if this is so?
IP's Blocked/ Block Count
UA 24 403
IN 77 312
RU 153 264
DE 77 236
CZ 90 227
Final thought, I'm surprised to see that China is not in this list, we see a lot of activity from China.
Thoughts?
1:11 pm
Thanks for your input John. I really try to block individual attackers as far as possible and that's always been our focus: To have Wordfence recognize individual attacks. Country blocking is a last resort in my opinion - as I mentioned to another commenter here a moment ago.
Yes it is interesting China is not on the list. They have a firewall separating them from the rest of the world and that may block outbound attacks.
Mark.
12:46 pm
Thanks for such a comprehensive report. It's obvious the WordFence crew puts as much effort into monitoring as it does into the product itself. Greatly appreciated.
1:12 pm
Thanks Joe.
1:25 pm
If it's not something you consider a trade secret, it'd be really interesting to have a report on the attacks that Wordfence did not block automatically.
Maybe making a summary of the infections your Site Cleaning Service have addressed during 2016, on websites that already had WF active (or maybe some other security plugin, too) yet were still hacked.
1:28 pm
Hi Alfonso,
We have a way of tracking attacks we miss and it very rarely happens, for the simple reason that as soon as it does, we immediately determine the root cause and release a new firewall rule.
Mark.
10:32 pm
Just a comment on the 'Seychelles' ISP:
The ISP is Quasi Networks & although as you report, the netblock is registered to the Seychelles, the hosts are actually located in the Netherlands. I am in the UK & they are a mere 9 hops away with a response time of 20ms. If they were really in the Seychelles, the laws of physics would preclude such a speedy response time. There are a number of hosts on this network that are actively scanning for other vulnerabilities; I have logged probes on Telnet & Secure SMTP in addition to Wordpress.
Keep up the good work guys, Wordfence is an awsome product!
11:36 pm
The country IP ONLY indicates the country network used for the attack not the source of the attack as any smart attacker would VPN (more than once) to convolute and hide their source IP!
So country IP indicates little and only highlights inflected host IPs attacking not manual smart attacks.
12:02 am
Hi all, and a big thumbs up to all the good folks from Wordfence ! One question on the validity of this IP-based approach though. In a recent article, Brian Krebs discussed the attack on the DNC, allegedly perpetrated by Russian state-sponsored hackers. In this rather long piece, Brian states that "Based on what I’ve learned over the past decade [...] my sense is that if the Russians were responsible and wanted to hide that fact — they’d have left a trail leading back to some other country’s door." (https://krebsonsecurity.com/2017/01/the-download-on-the-dnc-hack/). With IP-spoofing still being an issue, how confident can you be that you are tracking the right vilain ? I have wondered for some time now why a country like Ukraine, that heavily depends on western support, should be the source of so much trouble. And seeing as how Russia is openly trying to destabilize the country, I can't help but wonder. What's your opinion on this?
Again, a big thank you for all your efforts, and a happy and successful 2017 to you and your team.
1:31 pm
Wordfence has been a mainstay in my business for years and has saved my site from being compromised many times. This is a great report, thank you for putting it together. It appears that there is a lot of talent in Russia and Ukraine that could be put to much better use. Or, that ISPs could do a better job of policing their customers.
10:12 pm
Historically, I see a huge increase in attacks during the "holidays" - Christmas, Summer holidays, spring break, etc. So an increase starting Dec 15th and peaking right after Christmas was fully expected on my end.
The only thing that surprised me about France was that OVH wasn't higher in the list. I block those IP ranges now every single time. Iliad will be added to that list.
4:05 pm
Thank you for being so proactive, Mark. This form of communication with recent innovations and improvements in WordPress and Wordfence have not gone unnoticed. As low on the totem pole my website is, it is still being attacked, especially from China with its baidu.com spiders...not a biggie, but still can be a small nuisance. I do keep Wordfence up-to-date with automatic security and I must say they are doing a fantastic job. Although, I am young to all this, I do keep in contact with my hosting site, Arvixe. They, too, are doing a great job and have just upgraded to solid-state servers. Ending, thank you, again for all you and your team do. I love the latest update! All the best in 2017 and beyond.