This site uses cookies in accordance with our Privacy Policy.
3.8: The Tor Network – FAQ
Site owners concerned about security and privacy frequently have questions about Tor, the anonymity network and the applications like the Tor web browser that use the Tor network. We have compiled a list of Tor Frequently Asked Questions to try to efficiently address some of the more common questions that site administrators have about Tor.
What is Tor?
The name Tor comes from “The Onion Router” which was the early project name when it launched in 2002. Tor is a project that has created a network for routing anonymous traffic. The Tor network gives users a way to hide their location and hide which services they use or visit online.
The Tor network consists of Tor relays that route traffic. Tor is not just used for browsing the Web. It can be used by many applications that want to anonymously route traffic.
If an application wants to use the Tor network to anonymously route traffic, it talks to the Tor network using the SOCKS protocol. Applications like instant messaging, Internet Relay Chat (IRC) and web browsers can all use Tor to anonymously route traffic across the Internet.
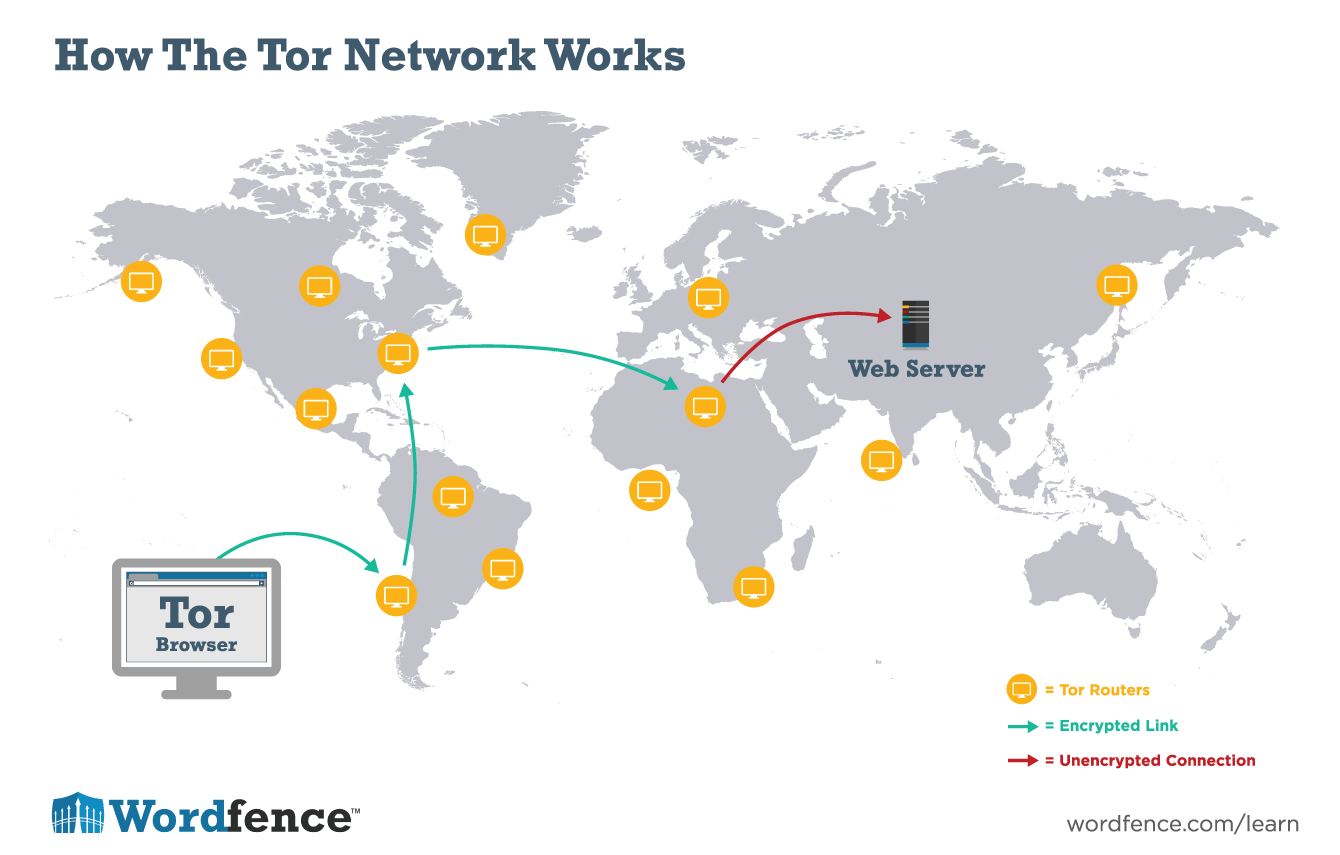
How Does Tor Work?
Tor routes traffic through the Tor network. As we mentioned above, Tor can be used by many applications, but let’s use a web browser as an example. If you are using Tor to connect to a server, your browser will establish an encrypted link with a Tor server. It will then establish a path or circuit through the Tor network. This path routes your traffic through several Tor servers and the path is random and changes every 10 minutes.
Once a path has been established through the network, your packets are routed from one server to the next. On the network, any given server only knows about the server that it received data from and the next server in the chain where it will send data to. No one server knows the entire path your traffic takes through the network. This prevents anyone from knowing where the traffic was sent from and where it is going to.
Tor encrypts traffic using a layering scheme which is where the Onion metaphor comes from. As traffic passes through nodes in the Tor network, a layer of encryption is stripped off at each node, much like the layers of an onion.
When using the Tor browser, traffic is encrypted between the browser and the Tor network. It is routed anonymously through the network and the very last node, the “exit node” uses an unencrypted link to communicate with a destination server outside the Tor network. It’s important to note this final hop is not encrypted.
Is Tor Evil?
Much like typewriters and printing presses, Tor can be used for good or evil. Tor is used by political dissidents worldwide to hide their location. It is used by employees visiting foreign countries to hide their traffic when accessing their employer’s servers back home. Tor is used by people living under oppressive regimes to access servers and websites that would otherwise be blocked by their governments.
Unfortunately Tor is also used for illegal activity. This includes child pornography, drug dealing, arms trading and other illegal commerce and activity.
What is a Tor Hidden Service?
Besides providing anonymous browsing and routing, Tor also provides a way to host a website or service online anonymously. Tor hidden services are websites that have the .onion top-level-domain (TLD).
An example Tor hidden service might be https://s34s4txr3vy22gpip.onion/
Most Tor hidden services are not human readable because they are generated using a cryptographic algorithm. It is possible using a lot of CPU power to create somewhat custom named hidden services. Facebook has their own Tor hidden service which you can access using a Tor browser at: https://facebookcorewwwi.onion/
Many websites that exist in the “Dark Web” (the hidden web that is not indexed by Google) exist as Tor hidden services.
Is Tor Completely Anonymous?
There is a lot of energy both in government and the private sector dedicated to defeating Tor anonymity. It has not been conclusively proven that Tor is not anonymous, but vulnerabilities in Tor and associated software continually emerge and are fixed.
It has been shown that it is possible to monitor traffic from a Tor exit node (the last hop in the Tor network) and the destination server because that traffic is not encrypted. If you were, for example, to send personally identifiable information through a Tor exit node and someone was monitoring that exit node, your identity would be revealed.
Hacking Team, a Milan based information security company who was hacked, developed a method to attack a Tor user’s anonymity via their local network. They attack the Tor user’s workstation. The attack then reconfigures their Tor browser to use the hacker’s own Tor network which lets them monitor traffic.
Other attacks that try to expose the identity of Tor users have targeted the Tor browser and vulnerabilities in the browser. If an attack is able to get the browser or user’s workstation to execute code, they can have that browser connect directly to a server on the Internet, bypassing the Tor network, which would expose that user’s identity.
It’s worth noting that Tor does not hide when you access a website or service. This is important because if you sign onto a website at the same time each day, someone may correlate your usage of the Tor browser with the exact time a website is visited each day and expose your identity.
Should I be blocking Tor Visitors to my Website?
Unless you have a specific problem or concern with Tor traffic, we recommend you allow Tor visitors to visit your website. As we mention above, Tor is used for good and evil. Occasionally hackers will use Tor to target a website or websites in order to mask their identity. If you are a target of this kind of attack, you can choose to block Tor exit nodes from visiting your site.
The Tor project publishes the list of Tor exit node IP addresses. The list is updated in real-time. You can find the list of Tor exit nodes currently in use on this page.
Should I be using Tor?
If you have concerns about your traffic being monitored, you can use Tor to hide the source and destination of your traffic. If you trust the security of Tor, your identity should not be revealed when you visit a website using the Tor browser.
Tor is useful for other things besides privacy. We occasionally use it to test IP blocking. We might configure a test server and want to verify that a certain IP blocking feature in Wordfence is working. Rather than blocking ourselves from the website we’re testing, we will use the Tor browser to break a security rule on our test website. Then we verify that the IP of our Tor browser (which is the IP of the exit node) has been blocked.
If we want to do the test again in Tor, we just restart the browser to get a different exit node which gives us a different IP address.
Conclusion
If you are interested in learning more about Tor, you can visit the Tor Project Overview to get another high level description of how Tor works. The Tor Browser is available in many different languages on this site. As we mention above, you can find a list of, or lookup Tor exit node IP addresses on this page. You can also visit the Tor FAQ which is very comprehensive. The Tor Network Wikipedia page provides a further description of the network.